Updated March 15, 2023

Introduction to Tomcat HTTPS
Tomcat HTTPS is when you want to run the web application on the HTTPS URL protocol, and this can only happen if you have configured an SSL certificate. In this article, we will discuss the overviews of tomcat HTTPS, configuration, tomcat redirection, and the step-by-step process to enable HTTPS in tomcat.
Tomcat HTTPS Overviews
Tomcat HTTPS is when you want to run the web application on the HTTPS URL protocol, and this can only happen if you have configured an SSL certificate. We can follow multiple approaches for certifying SSL, which are terminating the SSL that is secured socket layer at the load balancer or the given CDN level, we can implement the secured socket layer or implement SSL for which we can make the use of the available web servers including Apache Tomcat, Nginx, etc. in SSL front.
Tomcat HTTPS in Configuring
https can be specified in the connector tag of the server.xml configuration file of tomcat. For each module, we will have one element of XML. The XML file attributes are used to describe the properties of the module. Inside the configurations of the tomcat server, the Server.xml file is the main configuration file located at path TOMCAT_HOME/conf/server.xml. Inside TOMCAT_HOME/conf/name-of-server.xml file helps manipulate local system configurations that are read after the server.xml file.
Tomcat Redirect
We can set tomcat configurations so that all the requests are redirected from http to HTTPS. For this, open the server.xml located in TOMCAT_INSTALL/conf/ and set the redirection ports to the HTTPS port, 443. This can be done by changing the tag of the connector with the property as shown below –
redirectPort = “443” or any other port set for HTTPS.
You will also need to modify the web.xml file in configurations with the same changes. After that, all the requests of HTTP will be navigated to HTTPS.
all steps in detail enable HTTPS
- For directly enabling the tomcat in front-end or using the deployment of SSL inside the tomcat, we can follow the below-mentioned steps –
CSR, which stands for Certificate Signing Request, should be generated. - Inside the Keystore file, we need to import the certificate.
- Enable to Secured Socket Layer inside the Tomcat.
- TLS, which stands for Transport Layer Service protocol, should be configured
- Modify the configurations so that the tomcat starts listening on the 443 port address.
- SSL vulnerability should be checked and tested properly.
Let us discuss each of the steps in detail –
- CSR, which stands for Certificate Signing Request, should be generated. –
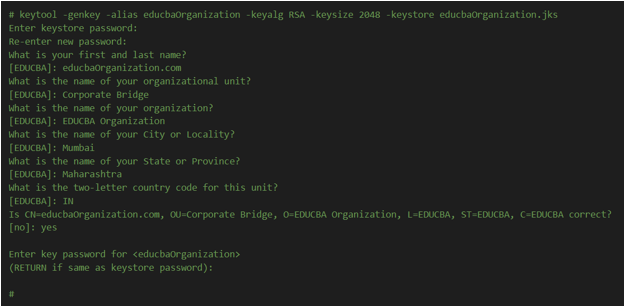
The symbol keytool in the utility will be used by us to control the management of the certificates. We will log in to the tomcat server and then navigate to the path where it was installed. Now, we will create a new folder named ssl and then execute the below-mentioned command that will make a Keystore for us –
Keytool -genkey -alias name_of_domain -keyalg RSA -keysize 1024/2048 -keystore name_of_file.jks
The name of the alias and the file should be kept to be easy to remember. The most suggested way is to give them the same name as the domain’s name.
For example, consider the below command –
# keytool -genkey -alias educbaOrganization -keyalg RSA -keysize 2048 -keystore educbaOrganization.jks
Enter keystore password:
Re-enter new password:
What is your first and last name?
[EDUCBA]: educbaOrganization.com
What is the name of your organizational unit?
[EDUCBA]: Corporate Bridge
What is the name of your organization?
[EDUCBA]: EDUCBA Organization
What is the name of your City or Locality?
[EDUCBA]: Mumbai
What is the name of your State or Province?
[EDUCBA]: Maharashtra
What is the two-letter country code for this unit?
[EDUCBA]: IN
Is CN=educbaOrganization.com, OU=Corporate Bridge, O=EDUCBA Organization, L=EDUCBA, ST=EDUCBA, C=EDUCBA correct?
[no]: yes
Enter the key password for <educbaOrganization>
(RETURN if same as keystore password):
#
When run on the terminal, the output is –
After this, you will receive the certificate from the certificate provider.
- Inside the Keystore file, we need to import the certificate.
Now, let us firstly import the certificate into Keystore. For doing this, we will execute the below command –
keytool -importcert -alias root -file root -Keystore educbaOrganization.jks
will import the root certificate in the key store the certificate provider provided. Now, we will execute the below command for importing the intermediate certificate –
keytool -importcert -alias intermediate -file intermediate -Keystore educbaOrganization.jks
In my case, I had only one intermediate certificate. If you have multiple intermediate certificates, then you need to import all of them. The final step of importing will be to import the domain certificate, which can be done by using the command –
keytool -importcert -file educbaOrganization.cer -Keystore educbaOrganization.jks -alias educbaOrganization
After importing all this, you will receive the installation confirmation, and the certificate Keystore will be all set.
- Enable to Secured Socket Layer inside the Tomcat and
- TLS, which stands for Transport Layer Service protocol, should be configured
Move to the conf folder of tomcat, which contains configurations. Take the backup of the existing file of server.xml and then move to the line stating
<Connector port = “8080” protocol = “HTTP/1.1”> and add the following new properties in the same tag –
Scheme = “https” SSLEnabled = “true” clientAuth = “false” sslProtocol = “TLS” keyPass = “payal” keystoreFile = “ssl/educbaOrganization.jks”
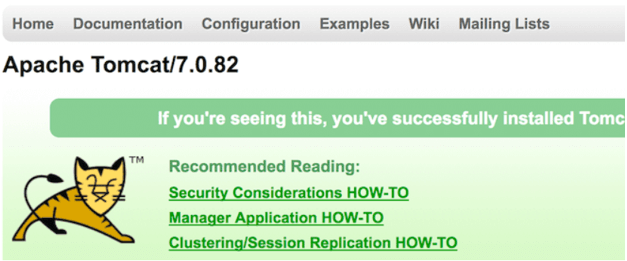
You should set the name of the Keystore and the corresponding password as per your credentials. After saving all the changes in the server.xml file, you need to restart the tomcat to make it accessible over HTTPS. Now, if you move to URL, https://educbaOrganization.com:8080 then you can see the tomcat home page as shown below –
- Modify the configurations so that the tomcat starts listening on the 443 port address.
Instead of 8080, the default tomcat port, we now want the system to listen on the 443 port. This is because we will not need to specify the port number in https:// URL to access tomcat. You can change the server.xml file, search for <Connector port = “8080,” and modify the specified port number to 443. After that, save the server.xml file and restart your tomcat. Now, if you type the URL https://educbaOrganization.com, it will open up the tomcat home page.
- SSL vulnerability should be checked and tested properly.
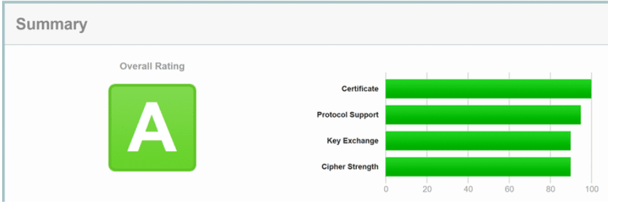
The last step is to check for any online threats and vulnerabilities in your domain. There are various online tools available in the market. We can make use of a tool called SSL labs. For this, you will first need to go to the SSL labs page, enter the URL of the domain whose SSL vulnerability test is to be made, and then begin the test. Observing all the ratings in green means your domain URL is not vulnerable to any threats. The output may look somewhat below –
Conclusion
We can set the configurations of the tomcat so that all the requests made on the HTTP protocol can be redirected to HTTPS. However, before that, you must enable HTTPS for tomcat by following the above steps.
Recommended Articles
This is a guide to Tomcat HTTPS. Here we discuss the Introduction, overviews, configuration, and examples with code implementation. You may also have a look at the following articles to learn more –