Introduction to Types of Attack
The term “types of attack” refers to the techniques employed by evil actors to penetrate digital systems, networks, or specific users, resulting in unauthorized access, data breaches, or system disruption. Knowing the range of attack types is essential for creating successful defense measures in the always-changing field of cybersecurity. Cyberattacks include phishing, ransomware, denial-of-service (DoS) attacks, and malware like viruses, worms, and trojan horses. Physical assaults include criminal acts like robbery, vandalism, and psychological tricks used to control others.
Hostile insiders or unintentional flaws exploit internal resources in insider attacks. In contrast to application attacks, which concentrate on utilizing software flaws, network attacks seek weaknesses in the network infrastructure. Social engineering assaults trick people into disclosing private information. Wireless assaults take use of flaws in wireless networks. In an increasingly linked world, awareness of various attack types enables people and organizations to bolster security measures, reduce risks, and protect digital assets.
Table of Content
Key Takeaways
- Cybersecurity is at risk from various attack types, including physical and social engineering techniques and cyber threats like malware, phishing, and ransomware.
- Understanding the range of attack vectors enables better defense strategies and proactive security measures to protect digital assets and personal information.
- A thorough defense against these assaults must include frequent software updates, robust authentication mechanisms, employee training, and network monitoring.
- A collaborative, knowledge-sharing culture and awareness of new risks are essential to sustaining a secure and robust digital environment.
Different Types of Attack
Below are the different types of attack as follows:
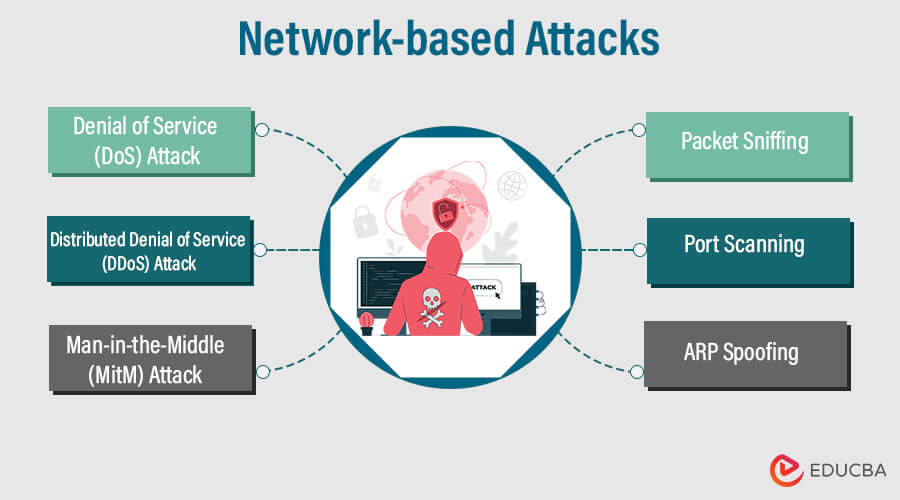
1. Network-based Attacks
Cybersecurity threats, known as network-based attacks, exploit holes in computer networks to obstruct operations, compromise data, or obtain unauthorized access. To achieve their harmful goals, these assaults target various network infrastructure components.
The following are descriptions of a few typical network-based attacks:
- Denial of Service (DoS) Attack: A Denial of Service attack seeks to prevent legitimate users from accessing a network resource or service by flooding it with excessive traffic or requests. Disruption or downtime occurs because the target system cannot respond to valid requests. Attackers can launch DoS attacks through various methods, such as saturating the target with traffic, exploiting security flaws, or executing resource-intensive queries.
- Distributed Denial of Service (DDoS) Attack: A distributed denial of service (DDoS), a more sophisticated denial-of-service attack, uses a botnet—a network of compromised devices—to flood a target with excessive traffic. The attack’s spread makes it challenging to stop the malicious traffic, which can quickly exhaust the target’s resources and cause considerable downtime.
- Man-in-the-Middle (MitM) Attack: When an attacker stealthily intercepts and relays communications between two parties, it is known as a Man-in-the-Middle (MitM) assault. The attacker secretly relays, modifies, or blocks messages transmitted between the parties. As a result, the attacker may be able to eavesdrop on conversations, steal login information, or intercept confidential data.
- Packet Sniffing: Capturing and analyzing data packets sent over a network is known as packet sniffing, often called packet interception or network sniffing. Attackers can intercept unencrypted network traffic using packet sniffing tools to obtain sensitive data, such as usernames, passwords, or confidential information. This attack may be more dangerous when sensitive data is delivered in clear text.
- Port Scanning: Attackers can use the port scanning approach to locate open ports and services on a target system or network. The attacker can find potential entry points for exploitation by searching for open ports. The attacker may attempt unauthorized access, initiate additional assaults, or exploit known vulnerabilities associated with the services operating on the identified vulnerable ports.
- ARP Spoofing: The assault known as ARP (Address Resolution Protocol) spoofing, often referred to as ARP poisoning, entails the perpetrator sending phony ARP messages to link their MAC address to the IP address of a trusted network device. The attacker can enable a man-in-the-middle attack by intercepting or changing network traffic for the legal device. ARP spoofing enables the possibility of data interception, session hijacking, and other network-based attacks.
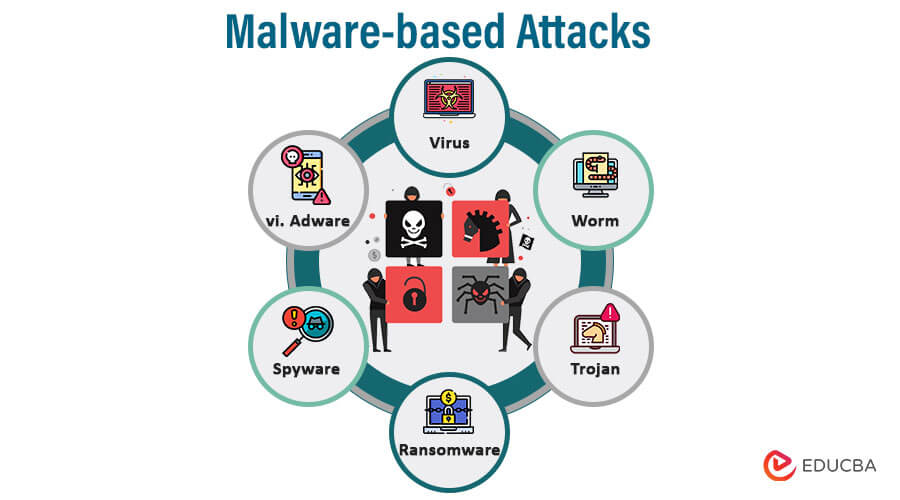
2. Malware-based Attacks
Any software intended to harm a computer system, network, or user is called malware, short for malicious software. Malware-based assaults involve the dissemination and execution of harmful software to infiltrate the target system and steal data, interfere with operations, or gain unauthorized access.
The following details many malware-based attacks:
- Virus: A virus is a malware that affixes to a trustworthy program or file and spreads by infecting more files or programs on the same system. The virus activates and copies itself to propagate further when the infected program is run. Viruses can be programmed to carry out various malevolent tasks, such as corrupting data, deleting files, or interfering with a computer system’s operations.
- Worm: A worm is a type of malware that replicates itself without the aid of a host file. Without human intervention, it spreads itself and infects other systems by taking advantage of security flaws in computer networks. Worms have a high rate of network propagation, which uses up network capacity and harms targeted systems severely. Some worms are built to deliver payloads that carry out certain destructive operations, like data erasure or unauthorized access.
- Trojan: A Trojan, usually called a Trojan horse, is a sneaky type of malware that poses as trustworthy programs or files to mislead users into installing it. Once installed, the Trojan can give the attacker backdoor access, enabling them to take unauthorized control of the compromised system. Trojans can be used for several things, including stealing sensitive data, spreading other software, or carrying out espionage.
- Ransomware: Data belonging to the victim is encrypted by ransomware, which then demands payment to obtain the decryption key. Malware includes ransomware. When ransomware infects a system, the user is locked out of their files, making them unavailable until the ransom is paid. Ransomware attacks have the potential to be extremely damaging, resulting in data loss, business interruptions, and monetary losses for both individuals and businesses.
- Spyware: A type of software created to covertly gather data on a user’s activities without the user’s knowledge or consent is known as spyware. It can keep track of sensitive data, record keystrokes, log surfing patterns, and collect passwords. The attacker frequently receives the information after it has been gathered and can use it for various things, including identity theft, targeted advertising, or selling the data on the black market.
- Adware: Adware is a term for malware that shows unwanted advertisements on a user’s computer. Adware is also known as advertising-supported software. Even though adware is less harmful than other types of malware, it can be irritating and irksome. It frequently comes packaged with reliable software and may monitor user activity to show relevant adverts. Adware may occasionally transcend the line into more intrusive practices, irritating consumers.
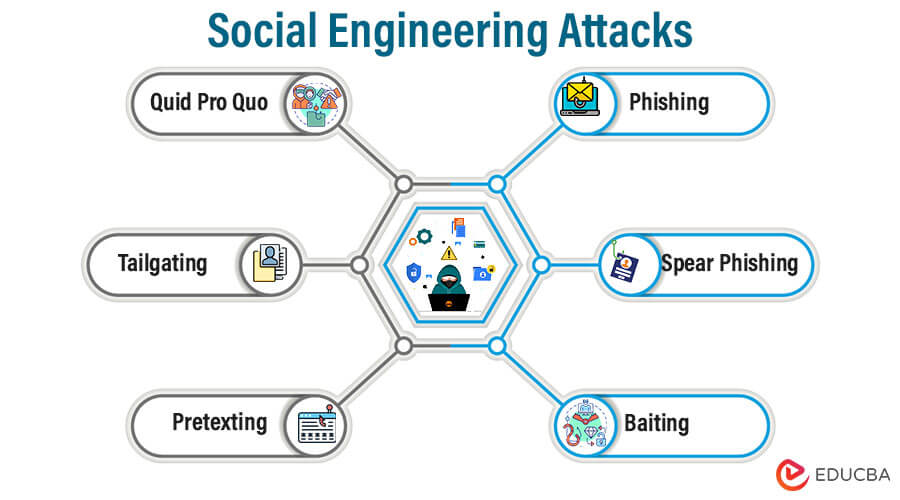
3. Social Engineering Attacks
Social engineering attacks are tactics cybercriminals use to manipulate individuals into revealing sensitive information, performing specific actions, or granting unauthorized access to computer systems or networks. Instead of targeting technical vulnerabilities, social engineering exploits the human element, relying on psychological manipulation and deception to achieve its objectives.
Below are explanations of various social engineering attack techniques:
- Phishing: One of the most prevalent social engineering attacks is phishing. In a phishing assault, the perpetrator sends phony emails, texts, or webpages pretending to be trustworthy businesses or organizations. Typically, the messages persuade the recipients to click on dangerous links, download malware, or submit private data like login passwords, credit card information, or personal information.
- Spear Phishing: A single person, business, or group of people is the target of a targeted kind of phishing called spear phishing. To create highly personalized and persuasive messages, the attackers gather information about the target, such as their name, position, interests, or contacts. Since the messages seem more real and pertinent to the recipients, this strategy raises the likelihood of success.
- Baiting: Baiting is persuading someone to perform a particular action by providing an alluring incentive, such as a free download, software update, or tangible object like a USB drive. When a victim falls for the bait and follows through with the activity, the attacker gains unauthorized access to the system or jeopardizes the user’s security. The bait may even contain malicious software.
- Pretexting: Pretexting is the fabrication of a false circumstance or pretext to lead others to divulge private information. To acquire the target’s trust, the attacker assumes a phony identity or position, such as that of a customer service agent or a coworker. They then manipulate the victim into divulging confidential data or performing actions they wouldn’t normally do under regular circumstances.
- Tailgating: Tailgating, also known as “piggybacking,” is when an unauthorized person physically enters a restricted area by trailing a permitted person very closely. An attacker might, for instance, appear pleasant and go with a worker who has access to a secure facility or area to acquire entry by abusing their trust.
- Quid Pro Quo: In a quid pro quo attack, the perpetrator offers the victim something beneficial in exchange for confidential information or access. For instance, the attacker might pose as an IT support specialist and offer to assist the victim in fixing a problem in exchange for their login or other private information.
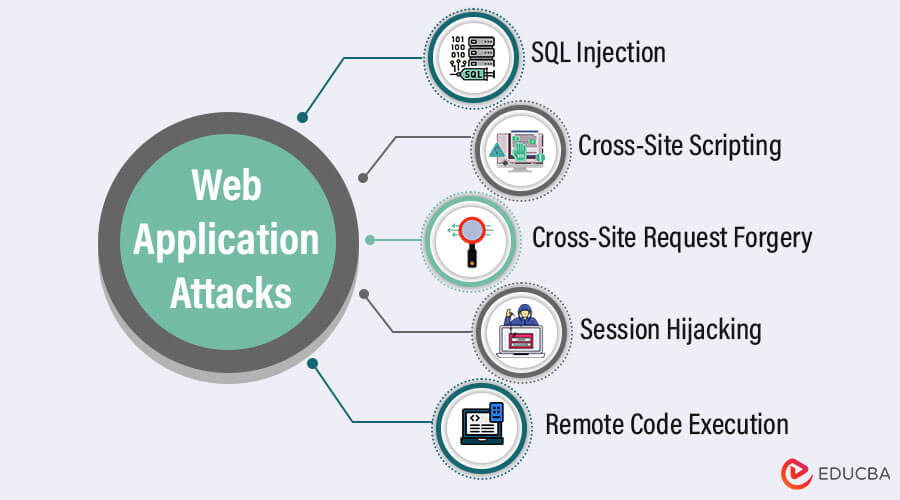
4. Web Application Attacks
Online application attacks are cyber threats that employ holes in online applications as entry points to compromise user data, obtain unauthorized access, or interfere with the application’s regular operation. Web apps are appealing targets for attackers because they frequently supply dynamic material and are accessible via web browsers.
The following details several typical web application attacks:
- SQL Injection: An attack known as SQL Injection (SQLi) involves manipulating an application’s input fields to insert malicious SQL code into the backend database query. The inserted SQL code could execute unwanted database commands, potentially giving the attacker access to sensitive data or enabling them to edit, destroy, or steal data if the web application does not adequately validate and sanitize user inputs.
- Cross-Site Scripting (XSS): When an attacker inserts harmful scripts into web pages that other users see, this is called cross-site scripting (XSS). The malicious script runs using the victim’s browser context, giving the attacker access to cookies, session tokens, and other private data. XSS attacks can potentially result in web page tampering or user redirection to malicious websites.
- Cross-Site Request Forgery (CSRF): The Cross-Site Request Forgery (CSRF) attack deceives authenticated users into unintentionally using a web application without their knowledge. The attacker creates a fraudulent request and then inserts it into an authentic email or web page. The request is automatically submitted using the victim’s authenticated session when the victim accesses the page or clicks the link, leading to undesired activities like updating account settings or performing fraudulent transactions.
- Session Hijacking: An attacker takes or intercepts a user’s session identifier during session hijacking, also known as session stealing or session sidejacking, to gain unauthorized access to their account. Attackers can carry out this via eavesdropping on unencrypted network connections or exploiting holes in the session management system of the online application. Once control of the session has been gained, the attacker can act on behalf of the victim by impersonating them.
- Remote Code Execution: In a serious online application vulnerability known as remote code execution (RCE), a hacker can run arbitrary code on the web server. RCE happens when an application fails to adequately check user inputs and permits malicious code injection, such as operating system commands or scripts. The attacker might take full control of the hosting environment and the web server if the vulnerability is successful.
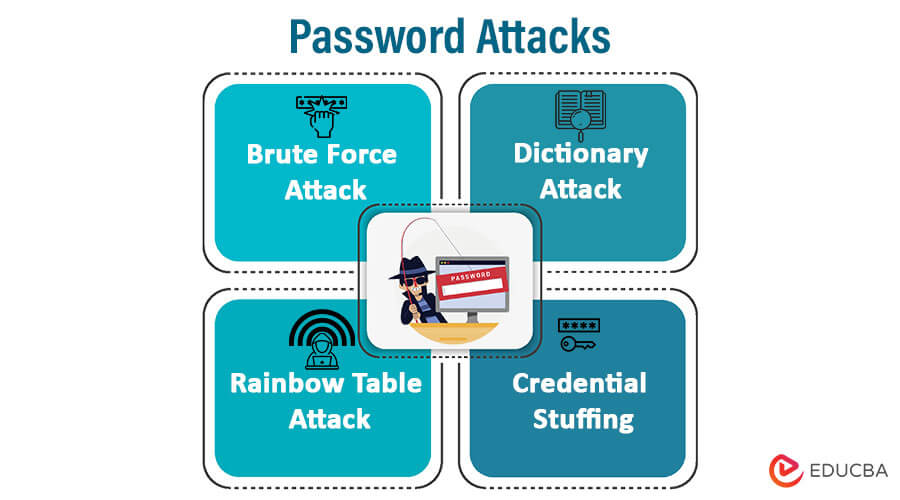
5. Password Attacks
Password attacks are strategies attackers employ to exploit weak or compromised passwords to obtain unauthorized access to user accounts or systems. These assaults try to defeat authentication protocols by deciphering or guessing passwords.
Below are details of various Password attack techniques:
- Brute Force Attack: During a brute force attack, the attacker iteratively attempts every conceivable character combination in search of the right password. Although time- and resource-consuming, this technique can be used to crack passwords that are too simple or short. Brute-force attacks involve using manual or automated methods to attempt various password combinations swiftly.
- Dictionary Attack: To attempt authentication, a dictionary attack uses a predetermined collection of words, phrases, or passwords from a “dictionary.” The attacker uses each word on the list as the password for the targeted account. Dictionary attacks outperform brute force assaults because they focus on passwords that many users are likely to use.
- Rainbow Table Attack: Using pre-calculated tables containing password hashes and their matching plaintext passwords, rainbow table attacks are a specialized type of password cracking. The password associated with a given hash can be rapidly looked up using these tables by the attacker. Systems often use cryptographic salts to guard against this attack, which adds random data to each password before hashing and greatly reduces precomputed tables’ effectiveness.
- Credential Stuffing: This attack technique tries to gain unauthorized access to other websites by using previously disclosed login and password combinations from one website or security breaches. Because many people use the same passwords on numerous websites, attackers employ automated tools to test these well-known username/password combinations on different platforms to access more accounts.
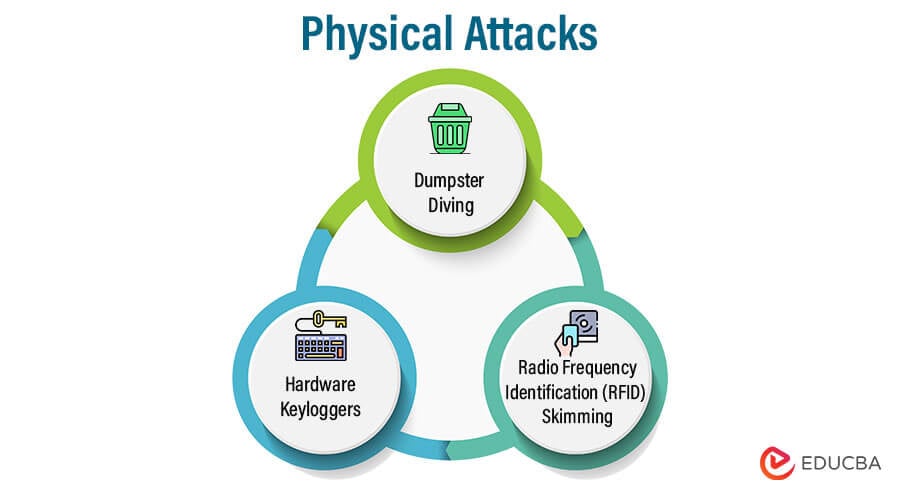
6. Physical Attacks
Physical attacks are cybersecurity threats that use flaws in the physical world to access information without authorization, steal sensitive information, or jeopardize security. These assaults focus on people, objects, or environmental flaws rather than exploiting software or network vulnerabilities.
The following are descriptions of typical physical attack techniques:
- Dumpster Diving: Dumpster diving searches for private information through trash or other abandoned items. Attackers might go through trashed electronic devices, documents, or receipts for information they can use, like login credentials, financial data, or proprietary materials. Dumpster diving can be particularly dangerous if businesses forget to destroy documents before throwing them away and fail to dispose of sensitive information properly.
- Hardware Keyloggers: Insert hardware keyloggers between the keyboard and the computer. They keep track of all keyboard inputs, passwords, credit card numbers, and other private data. Hardware keyloggers present a significant security concern in settings without strict physical access regulations to computers due to their discreet installation and challenging detection.
- Radio Frequency Identification (RFID) Skimming: RFID skimming is the practice of reading or capturing data from radio frequency identification (RFID) cards, such as contactless credit cards, access badges, or electronic passports, using electronic devices. Attackers using RFID skimming equipment can take sensitive data without contacting the cardholder directly. They can then access secure areas without authorization or carry out unauthorized transactions using the stolen data.
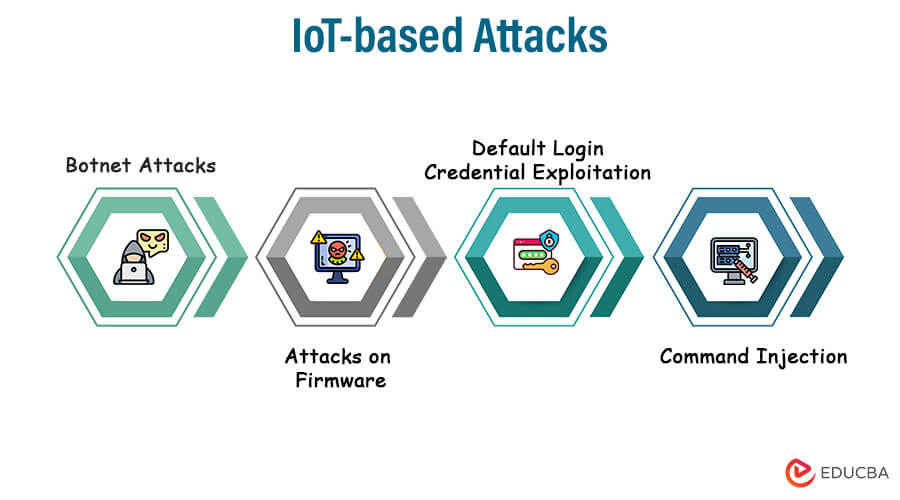
7. IoT-based Attacks
IoT-based attacks are cyber threats that target Internet of Things (IoT)-connected devices. IoT devices have connectivity, software, and integrated sensors that gather and exchange data online, turning them into commonplace items. These assaults take advantage of flaws in IoT devices to take control of them, interfere with their performance, or use them as weapons in other assaults.
The following descriptions outline a few typical attack techniques based on IoT:
- Botnet Attacks: In a botnet attack, IoT devices are infected with malware that enables remote command-and-control (C&C) server control of the devices. The infected machines, sometimes referred to as bots or zombies, can work together to execute various harmful tasks, such as spamming, conducting distributed denial of service (DDoS) assaults, and engaging in crypto-jacking. Due to their capacity to conduct coordinated, large-scale attacks using the combined computing power of numerous infected devices, botnets are particularly dangerous.
- Attacks on Firmware: Firmware, or embedded software, is the subject of attacks on firmware. Attackers may take advantage of flaws in the firmware to take control of the device or alter its functionality. Attackers can take over a gadget, change its behavior, or make it unusable by compromising the firmware. These attacks can last long because users rarely apply firmware updates.
- Default Login Credential Exploitation: Using the Default Password, Many IoT devices are delivered with pre-configured default login credentials (username/password combinations) to simplify initial configuration. Attackers can easily utilize these gadgets if users don’t update the default passwords. Using the default credentials, an attacker can obtain access to the device and take control of it, steal sensitive data from it, or use it as a launching pad to access other devices on the same network.
- Command Injection: An IoT device’s input to run unauthorized commands or code on the underlying system is a command injection attack. Attackers can conduct arbitrary commands on the IoT device or jeopardize its security by introducing malicious input into web forms, APIs, or other user interfaces. Vulnerabilities related to command injection might result in unauthorized data access, remote code execution, or even total control of the IoT device.
8. Insider Attacks
Referred to as insider attacks are cybersecurity threats that come from within a company’s ranks. Attackers using lawful access to an organization’s systems, data, or facilities are usually employees, contractors, or business partners who abuse their powers. Insider assaults can be deliberate or accidental, and they represent serious hazards to an organization’s security because they frequently benefit from access and levels of trust that are not available to external attackers.
The following are descriptions of typical insider assault types:
- Insider Threats: Individuals who intentionally behave maliciously to threaten a company’s security, reputation, or assets earn the designation of insider threats. These people could be vengeful ex-employees out for blood, those driven by greed, or insiders threatened or blackmailed by outside parties. Data breaches, intellectual property theft, sabotage, or the dissemination of false information are all possible outcomes of insider threats.
- Data Theft: Insiders can steal confidential or proprietary information from a company for their gain or sell it to rivals or other parties for a profit. Insiders may gain unapproved access to private information like financial data, trade secrets, customer details, or confidential data. Financial losses, reputational harm to the company, and legal repercussions can all occur from data theft.
- Sabotage: Insiders who participate in sabotage intend to disrupt an organization’s activities or harm its infrastructure actively. This may entail wiping out data, taking down vital systems, injecting malicious code into the network, or messing with processes to create havoc. Insider sabotage can cause a great deal of downtime, financial losses, and even reputational damage to the company.
How to Prevent Attacks?
A proactive and multi-layered strategy for cybersecurity is necessary to prevent assaults.
Here are some crucial actions you may take to protect your organization or yourself from various forms of attacks:
- Maintain Software and Systems: Regularly update your operating system, software programs, and security patches. By staying current, you can reduce the risks of attacks that take advantage of known vulnerabilities.
- Use Strong and Unique Passwords: Use obscure information sparingly, and never use the same password for several accounts.
- Enable Multi-Factor Authentication (MFA): Enable multi-factor authentication (MFA) when possible. By forcing users to give additional authentication factors, such as a one-time code delivered to their phone, in addition to their password, MFA strengthens security.
- Educate Users on Security Awareness: Users should be aware of security risks through regular security training and awareness campaigns informing them of attack techniques like phishing and social engineering. Teach kids to recognize and report shady activity.
- Back-Up Regularly: You should create and store regular backups of important data in a secure location. If you have backups, you can restore your data during a ransomware attack or data loss without paying a ransom.
- Secure IoT Devices: IoT device security tips include changing default passwords, routinely updating firmware, and separating IoT devices from key systems to reduce attack surfaces.
- Conduct Security Audits: To proactively find and fix vulnerabilities, regularly evaluate your organization’s security posture through internal or external security audits and penetration testing.
Conclusion
A wide range of attack types presents serious difficulties for cybersecurity. There is a clear need for all-encompassing defense mechanisms against physical and social engineering attempts and cyber threats like malware, phishing, and ransomware. Individuals and organizations can strengthen their security strategy, implement preventative measures, and remain vigilant against evolving threats by being aware of various attack vectors. We can improve our capacity to secure digital assets and ensure a safer and more resilient cyber world by fostering collaboration, sharing expertise, and staying updated about emerging dangers.
FAQs
Q1. What is a zero-day exploit?
Answer: A zero-day exploit seeks out software flaws that neither the program vendor nor the developers know. Attackers exploit these vulnerabilities before providing a patch or update, thereby exposing users to attacks until a fix becomes available.
Q2. How can I safeguard against insider threats?
Answer: Organisations might use stringent access controls, employee activity monitoring, background checks, and staff education to reduce insider threats.
Q3. How do wireless attacks exploit vulnerabilities?
Answer: Wireless assaults take advantage of flaws in wireless networks, like untrusted access points or the ability to eavesdrop on wireless conversations.
Recommended Articles
We hope that this EDUCBA information on “Types of Attack” was beneficial to you. You can view EDUCBA’s recommended articles for more information.