Introduction to Types of Computer Network
As our world becomes increasingly interconnected, networks have become essential to our daily lives. Networks are the lifeblood of our digital age, allowing us to communicate, collaborate, and explore the vast depths of information at our fingertips. But did you know there are various types of networks, each with unique characteristics and purposes? From the sprawling worldwide web to the intimate confines of your home, let’s embark on a journey to uncover the diverse realm of network types.
Table of Content
- Introduction to Types of Network
- Different Types of Network
Different Types of Network
There are various types of networks, each serving different purposes and use cases. Here is an extended list of network types:
Based on Size and Coverage
Networks can be classified into different types based on their size and coverage area, ranging from small local networks to large, global-scale networks. Here are some of the most common types:
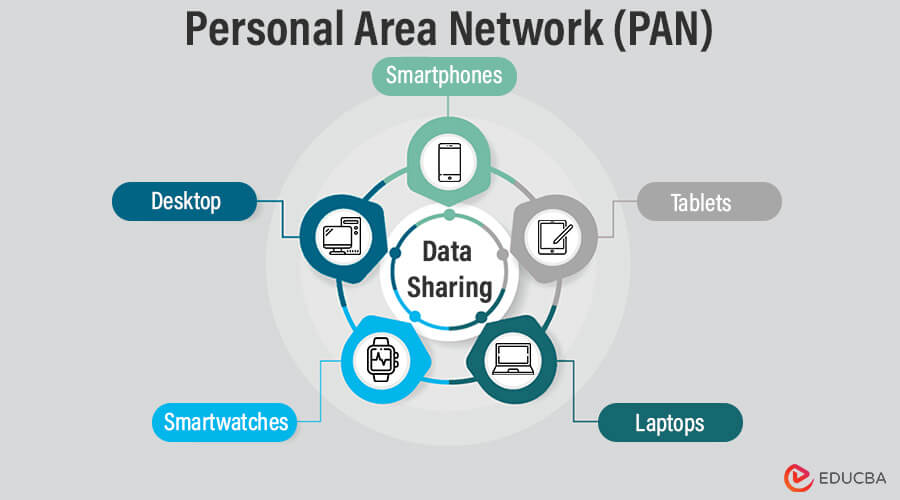
1. Personal Area Network (PAN)
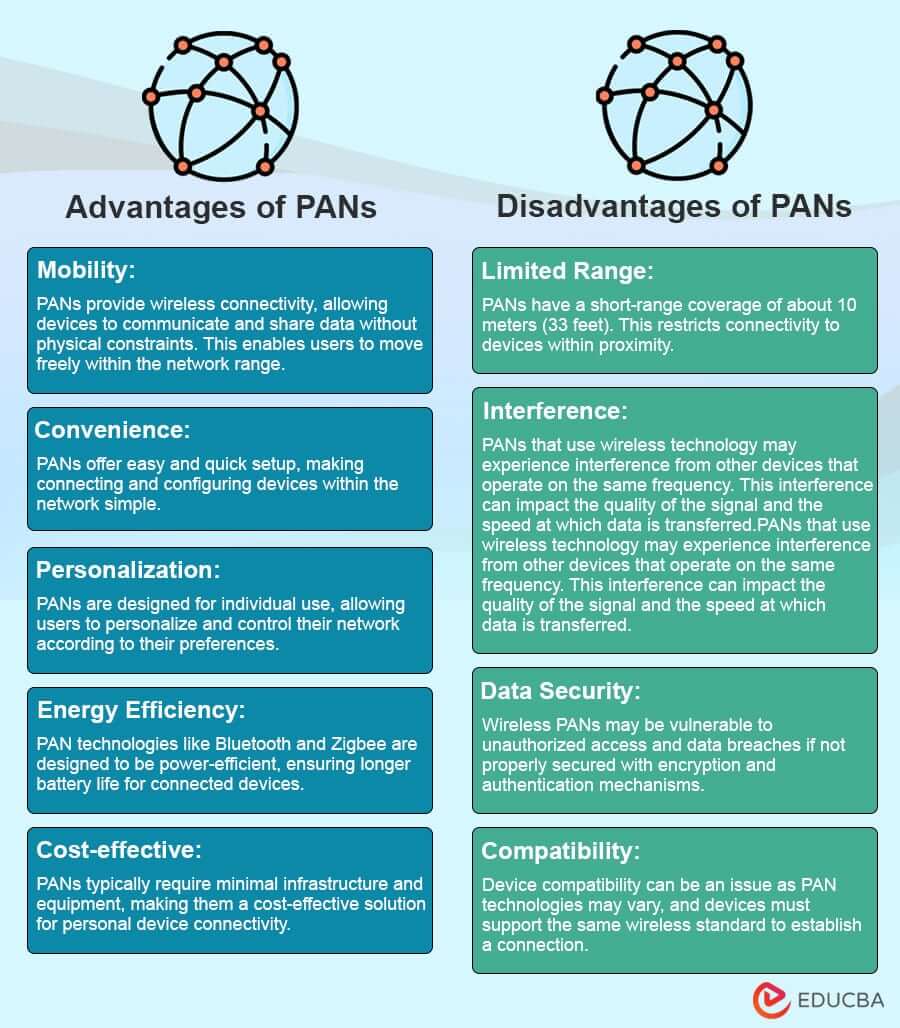
A Personal Area Network (PAN) connects devices within an individual’s immediate vicinity, typically within a range of about 10 meters (33 feet). It enables communication and data sharing between personal devices such as smartphones, tablets, laptops, smartwatches, and other wearable devices.
Types of PANs:
- Wired PAN: A wired PAN involves connecting devices using cables or wires. This type of PAN is less common than wireless PANs but can still be utilized in certain scenarios. For example, a wired PAN may be established using USB cables to connect devices like smartphones, tablets, and laptops to peripherals such as printers, keyboards, or external storage devices. This direct physical connection allows for reliable and high-speed data transfer.
- Wireless PAN: Wireless PANs are more prevalent in everyday use. They utilize wireless technologies to establish connections between devices without needing physical cables. Bluetooth is the most common wireless technology used for PANs, which enables devices within proximity to communicate and share data wirelessly. Bluetooth PANs can be easily set up and offer flexibility and mobility, making them ideal for personal device connectivity. Other wireless technologies, such as Zigbee and Wi-Fi Direct, can also create PANs, depending on the specific requirements and devices involved.
Uses of PANs:
- File Sharing: With PANs, users can easily transfer files between their smartphones, tablets, and laptops without interruptions.
- Peripheral Device Connectivity: PANs allow devices to connect wirelessly to peripherals like printers, keyboards, and speakers.
- Personal Device Synchronization: PANs facilitate the synchronization of data, such as contacts, calendars, and media, between personal devices.
- Audio Streaming: PANs enable wireless audio streaming to headphones, speakers, or car audio systems.
- Wearable Device Integration: PANs connect wearable devices like smartwatches, fitness trackers, and health monitors to smartphones or tablets.
Examples of PANs:
- Connecting a Bluetooth headset to a smartphone.
- Syncing a smartwatch with a smartphone to receive notifications and track fitness data.
- Transferring files between a laptop and a smartphone using Bluetooth.
- Printing wirelessly from a tablet to a Bluetooth-enabled printer.
- Connecting a mouse and wireless keyboard to a computer using Bluetooth.
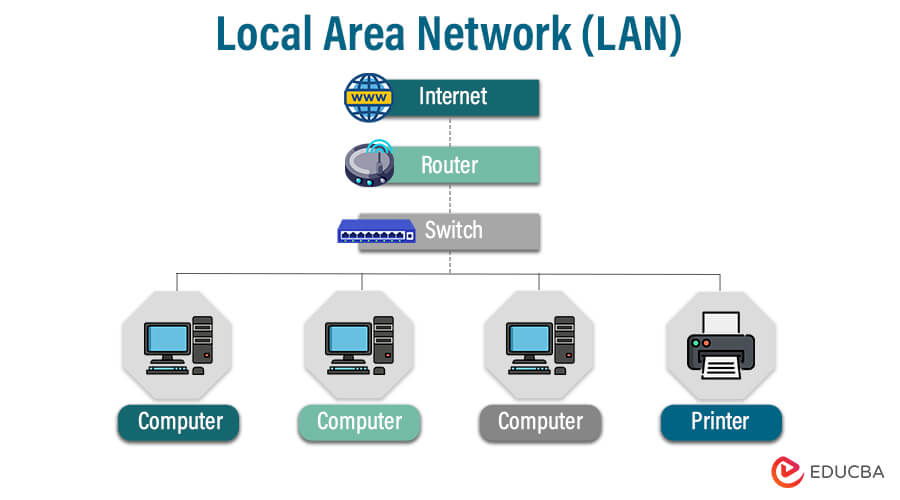
2. Local Area Network (LAN)
A LAN, or Local Area Network, allows devices to connect within a specific geographic area, such as a building, office, or home. This type of network is commonly used to facilitate communication and data sharing between computers and other devices. LANs are widely used to facilitate communication and resource sharing between connected devices.
Types of LANs:
- Token Ring LAN: Token Ring LANs use a token-passing protocol, where a special “token” is circulated among devices on the network. When a device possesses the token, it has the right to transmit data. Token Ring LANs ensure fair access to the network and are characterized by a ring topology.
- Token Bus LAN: Token Bus LANs also employ a token-passing mechanism, but instead of a ring topology, they use a bus topology. Devices on the network contend for the token to transmit data. Token Bus LANs were less commonly used than Token Ring LANs.
- Wireless LAN (WLAN): WLANs use wireless technology, such as Wi-Fi, to connect devices without needing physical cables. They allow users to access the network and its resources via wireless adapters or devices with built-in Wi-Fi capabilities. WLANs provide flexibility, mobility, and ease of connectivity.
- Wired LAN: Wired LANs utilize physical cables, such as Ethernet or fiber optic cables, to connect devices within a limited area. They offer reliable and high-speed data transfer rates. Wired LANs are commonly used in offices, homes, and data centers.
- Cloud Managed LAN: Cloud Managed LANs leverage cloud-based management and control to centrally administer and monitor the LAN infrastructure. Network configuration, monitoring, and troubleshooting can be done through a web-based interface, providing scalability, ease of management, and simplified network deployment.
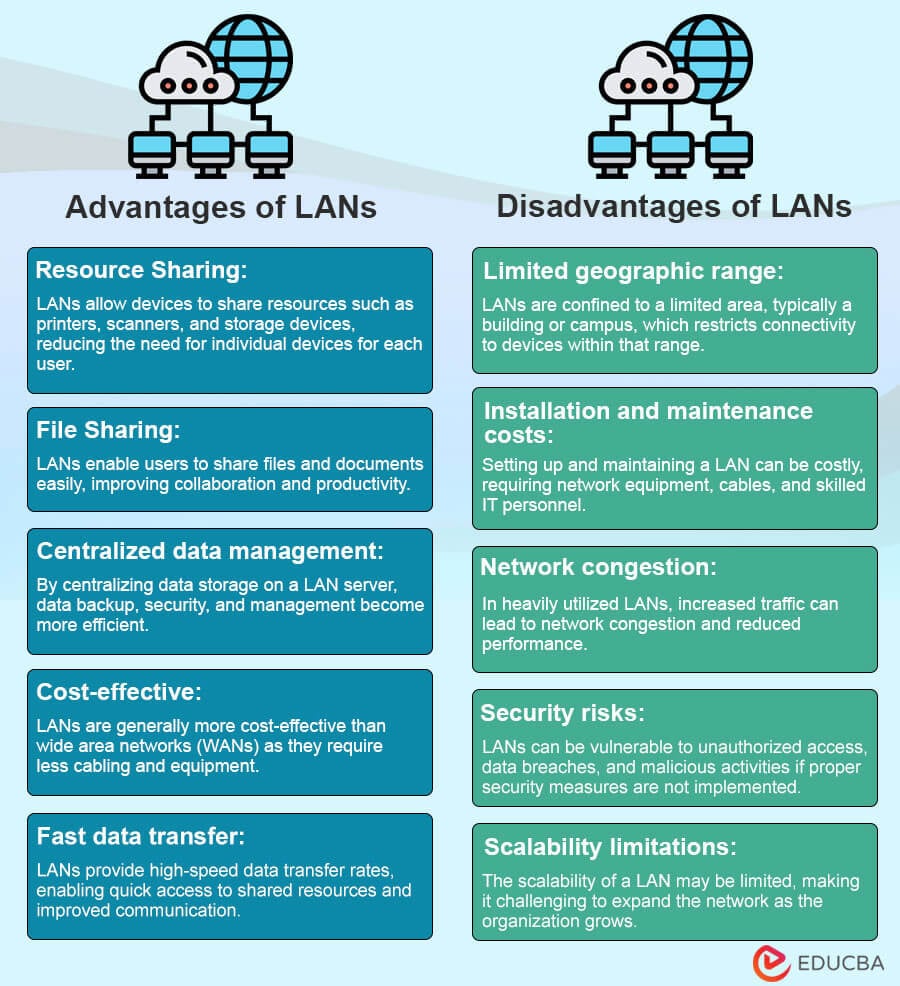
Characteristics of LANs:
- Limited geographical area: LANs cover a small physical area, typically within a building or campus.
- High data transfer rates: LANs provide fast data transfer rates, allowing quick communication and resource sharing.
- Localized administration: LANs locally manage and administer network resources, allowing control over them.
- Shared infrastructure: LANs often use shared network infrastructure, such as Ethernet switches and routers, to connect devices.
Purposes of LANs:
- Facilitating communication: LANs enable users to communicate through email, instant messaging, and shared applications, improving collaboration within an organization.
- Resource sharing: LANs allow multiple users to share resources like printers, scanners, and storage devices, reducing costs and improving efficiency.
- Centralized data storage and backup: LANs provide a centralized location for storing and backing up important data, making it easily accessible and protected.
- Access to shared applications and databases: LANs allow users to access shared applications and databases, enabling streamlined workflow and access to critical information.
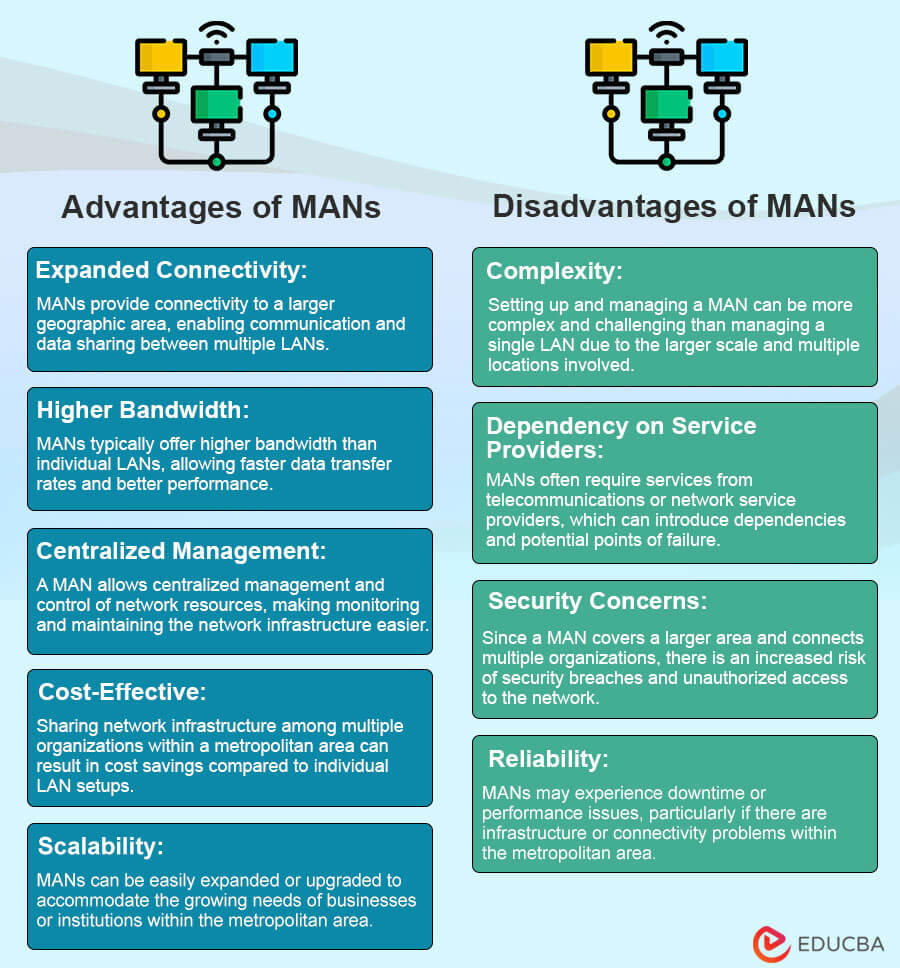
3. Metropolitan Area Network (MAN)
A Metropolitan Area Network (MAN) is a computer network that spans a metropolitan area or a city. It connects multiple local area networks (LANs) and efficiently transmits data, voice, and video between different locations within the metropolitan region.
Examples of MAN:
- Cable Television Network: Cable TV providers often leverage MANs to deliver television signals and internet services to subscribers within a city or metropolitan area.
- Educational Institutions: Universities and colleges often establish MANs to interconnect various departments, libraries, and research facilities.
- Government Networks: Municipalities or government agencies may use MANs to connect different government buildings, enabling efficient communication and data sharing.
- Large Corporations: Multinational companies or corporations with multiple branches in a city can employ a MAN to connect their various offices and facilities.
Types of MAN:
- Fiber Distributed Data Interface (FDDI): FDDI is a type of MAN that uses fiber optic cables to transmit data over a ring network topology.
- Asynchronous Transfer Mode (ATM): MANs use ATM as a high-speed networking technology to efficiently transmit voice, data, and video.
- Ethernet MAN (E-Man): E-Man utilizes Ethernet technology to connect multiple LANs within a metropolitan area, providing a cost-effective solution for interconnecting local networks.
- Wireless MAN (WMAN): WMANs use wireless communication technologies like Wi-Fi or WiMAX to establish a wireless network within a metropolitan area.
It’s important to note that the classification and availability of specific MAN types may vary as network technologies evolve and improve over time.
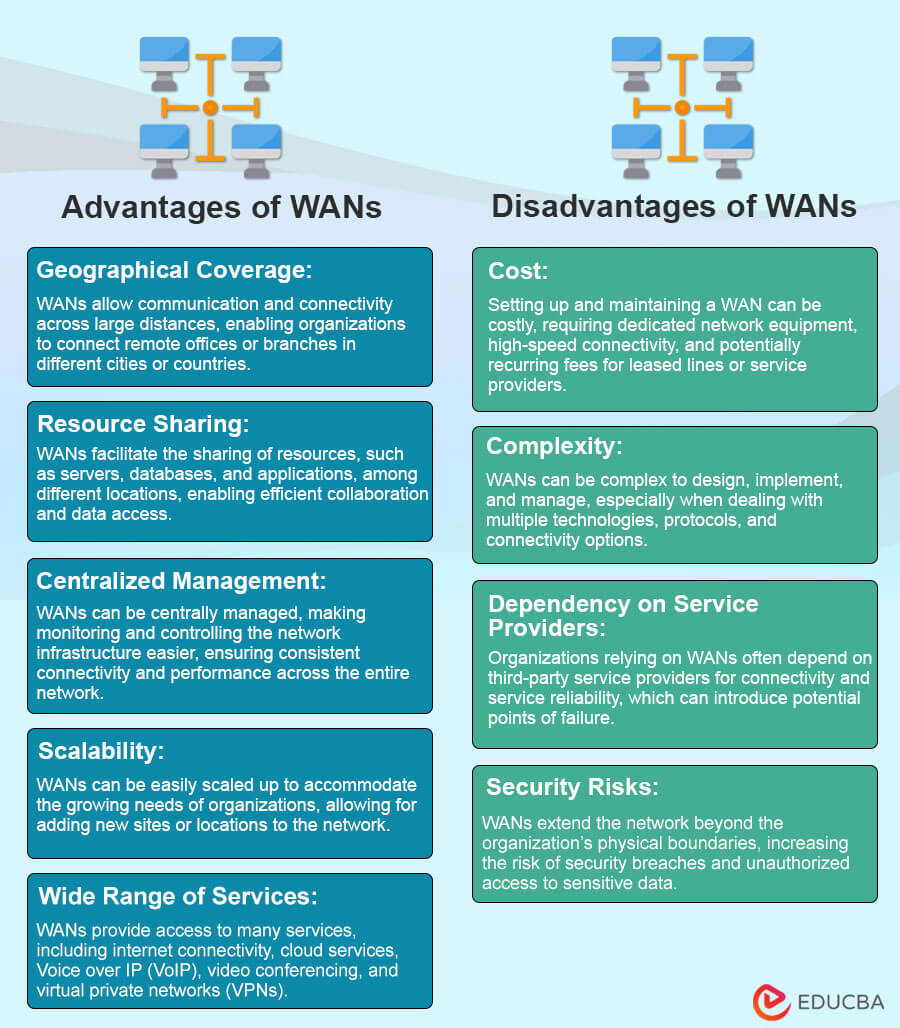
4. Wide Area Network (WAN)
A Wide Area Network (WAN) is a computer network spanning large geographical areas, such as cities, countries, or continents. It connects multiple Local Area Networks (LANs) or other WANs together, allowing for data, voice, and video transmission over long distances. Many organizations use WANs to connect their remote offices, branches, or data centers, enabling communication and resource sharing.
Examples of WAN:
- Virtual Private Network (VPN): VPNs create secure tunnels over public networks, such as the internet, to connect remote locations and enable secure communication and resource sharing.
- Internet-based WAN: Many organizations leverage the internet as a WAN infrastructure, using technologies like IPsec, MPLS, or software-defined WAN (SD-WAN) to connect their remote sites.
- Leased Lines: Leased lines, such as T1/E1 or T3/E3 lines, provide dedicated point-to-point connections between locations, ensuring reliable and secure data transmission.
- Satellite Networks: In remote areas or regions with limited terrestrial infrastructure, WANs can be established using satellite communication technology to connect sites over long distances
Characteristics of WAN:
- Large Geographic Coverage: WANs cover a significant geographic area, ranging from regional, national, or international scopes.
- Diverse Connectivity Technologies: WANs use various technologies, including leased lines, fiber optics, satellite links, microwave connections, and internet-based networks, to establish connectivity between different sites.
- Reliance on Public or Private Infrastructure: WANs can utilize public networks, such as the internet, or private leased lines to transmit data, depending on the organization’s requirements and security considerations.
- Network Protocols and Routing: WANs employ routing protocols, such as Border Gateway Protocol (BGP), to efficiently direct data packets across multiple interconnected networks and determine the best path.
- Quality of Service (QoS): WANs often implement QoS mechanisms to prioritize certain types of traffic, such as voice or video, to ensure optimal performance and minimize latency for critical applications.
Types of WAN:
1. Packet switching: Two main types of packet switching are used in wide area networks (WANs): circuit-switched and packet-switched. Let’s explore both types:
- Circuit-Switched WAN: In a circuit-switched network, a dedicated communication path is established between two endpoints for the duration of the communication session. This path remains dedicated to the specific session, even without data transmission. Traditional telephone networks are an example of circuit-switched networks. Circuit-switched networks provide guaranteed bandwidth but are less efficient for data transmission than packet-switched networks.
- Packet-Switched WAN: A packet-switched network divides data into packets and transmits them independently. The packets can take different routes and reassemble at the destination. Packet-switched networks are more efficient for data transmission as they allow multiple sessions to share the same network resources. The internet is an example of a packet-switched network.
2. TCP/IP protocol suite: The TCP/IP protocol suite is the foundation for communication on the internet and many private networks. It consists of two main protocols:
- Transmission Control Protocol (TCP): TCP provides reliable, connection-oriented communication between devices. It ensures the delivery of data packets in order, without errors, and incorporates flow control mechanisms to prevent congestion. TCP breaks data into packets, reassembles them at the destination, and ensures error recovery in the event of any lost packets.
- Internet Protocol (IP): IP addresses and routes packets across networks. It establishes the logical addressing scheme used for identifying devices on a network and enables the routing of packets to their destinations. IP handles the fragmentation and reassembly of packets and ensures their proper delivery.
3. Packet over SONET/SDH (PoS):
Packet over SONET/SDH is a technology that allows for transmitting packet-switched data over synchronous optical networks (SONET) or synchronous digital hierarchy (SDH) networks. Standardized protocols for transmitting digital signals over optical fiber networks include SONET and SDH. PoS encapsulates IP packets into SONET/SDH frames, efficiently utilizing high-speed optical networks for IP-based data transmission.
4. Multiprotocol Label Switching (MPLS):
MPLS is a packet-forwarding technology in high-performance networks. It combines the benefits of circuit-switching and packet-switching to route IP packets efficiently. MPLS uses labels to identify paths through the network, allowing routers to make forwarding decisions based on these labels rather than examining the entire packet’s IP header. This improves the speed and efficiency of routing, enhances quality of service (QoS) features, and enables the creation of virtual private networks (VPNs) and traffic engineering in complex networks.
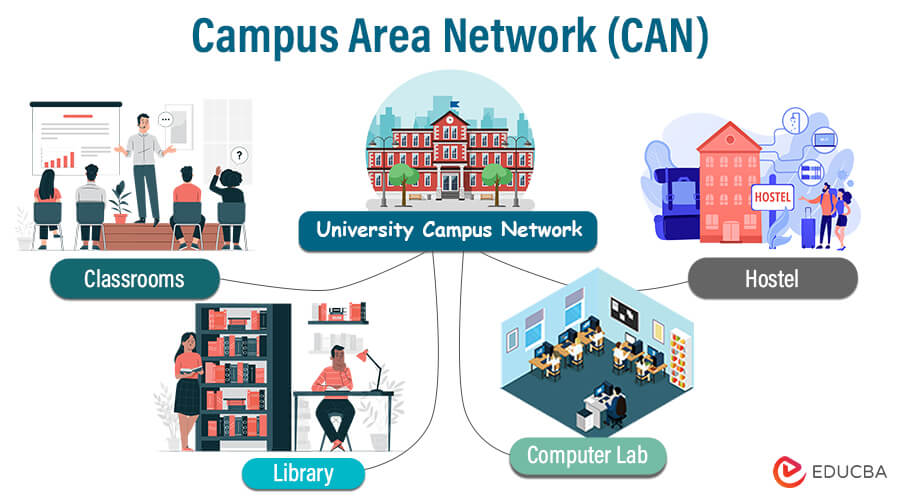
5. Campus Area Network (CAN)
A Campus Area Network (CAN) is a type of computer network that interconnects multiple buildings or facilities within a limited geographic area, such as a university campus, corporate campus, or military base. Its design aims to facilitate high-speed communication and data sharing between different departments, offices, and resources within the campus.
Examples of CAN:
- Educational Institutions: Universities and colleges often utilize CANs to interconnect academic buildings, research centers, libraries, and administrative offices. It enables seamless collaboration, access to shared resources, and efficient communication across the campus.
- Corporate Campuses: Large organizations with multiple buildings or branch offices close can establish a CAN for seamless internal communication, resource sharing, and centralized IT management.
- Government or Military Facilities: Government agencies, military bases, and research centers commonly use CANs to connect various facilities, command centers, and administrative offices within the campus area.
- Healthcare Campuses: Hospitals or medical complexes may deploy a CAN to connect different departments, clinics, and healthcare facilities, allowing for streamlined communication and secure sharing of patient data
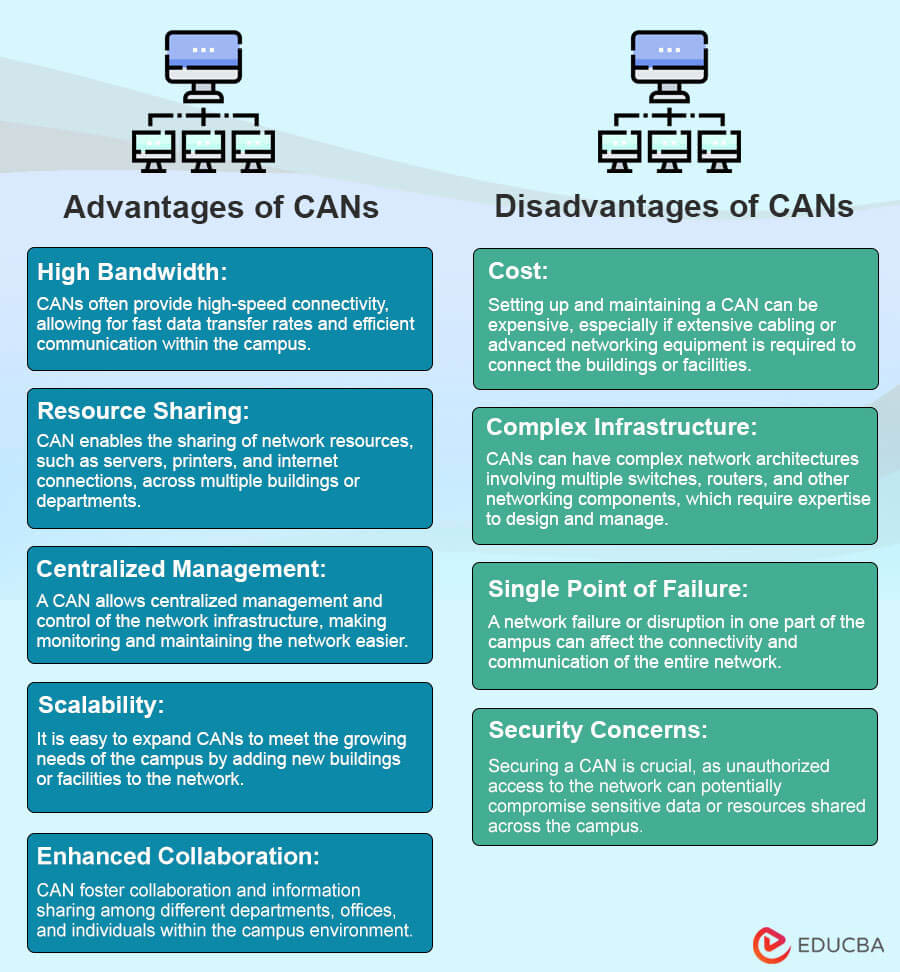
Characteristics of CAN:
- Geographical Scope: CANs cover a limited geographic area, typically within a single campus or a close grouping of buildings.
- High-Speed Connectivity: CANs provide high-speed data transmission capabilities, allowing efficient communication and resource sharing.
- Wired and Wireless Infrastructure: CANs may incorporate wired and wireless technologies to connect the buildings and facilitate network access for various devices.
- Scalability and Flexibility: CANs allow for easy expansion and adaptation to accommodate the changing needs of the campus, making them scalable and flexible in design.
Based on Scale and Purpose
Various network types can be categorized according to their scale and purpose. Here are several typical network classifications:
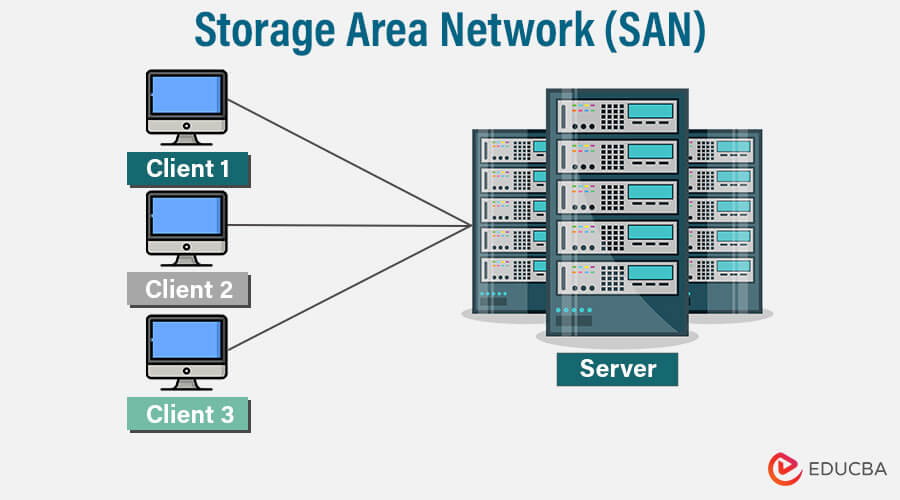
1. Storage Area Network (SAN)
A Storage Area Network (SAN) is a specialized network infrastructure that provides high-speed, block-level access to consolidated storage resources. SANs are designed to centralize storage and provide efficient, scalable, and secure data storage and retrieval capabilities.
Components and Architecture of a SAN:
- Storage Devices: SANs include storage devices like disk arrays, tape libraries, or solid-state drives (SSDs). These devices are connected to the SAN fabric and managed centrally.
- SAN Fabric: The SAN fabric comprises switches, hubs, and routers that interconnect storage devices and servers. Fibre Channel (FC) or Ethernet-based protocols like Fibre Channel over Ethernet (FCoE) are commonly used in SAN fabrics.
- Host Bus Adapters (HBAs): Servers or computing systems in a SAN environment require HBAs, which are specialized network interface cards (NICs). HBAs enable servers to connect to the SAN fabric and access the shared storage resources.
- Storage Management Software: SANs employ storage management software for tasks such as provisioning, volume management, data replication, and backup. These software tools provide centralized control and monitoring of the SAN infrastructure.
2. Content Delivery Networks ( CDNs)
A Content Delivery Network (CDN) is a collection of servers or edge locations spread across different locations. The main function of a CDN is to provide faster, more secure, and more reliable delivery of web content, such as web pages, images, videos, and other resources to end-users.CDNs are an integral part of modern Internet infrastructure and play a crucial role in optimizing content delivery across the Internet.
Purpose of CDNs
The primary purpose of CDNs is to optimize the delivery of web content and applications. This includes:
- Speed: CDNs improve user experience by reducing latency and accelerating content delivery.
- Availability: CDNs ensure that content is available even during traffic spikes or server failures.
- Security: CDNs protect websites and applications from threats such as DDoS attacks and help to secure data during transit.
- Bandwidth Management: CDNs, or Content Delivery Networks, are used to effectively manage and optimize bandwidth usage, which helps reduce costs and improve overall performance.
Types of CDNs:
- Web CDNs: CDNs are commonly used to optimize web content such as images, CSS, and JavaScript files.
- Video Streaming CDNs: CDNs are specifically designed to optimize the delivery of video content, ensuring smooth and uninterrupted streaming while minimizing buffering.
- Application CDNs: These CDNs are tailored for dynamic, database-driven applications, ensuring fast response times for application data.
- DNS CDNs: These CDNs optimize domain name resolution for faster website access.
- IoT CDNs: CDNs for IoT are designed to distribute data from IoT devices efficiently.
- Mobile CDNs: These CDNs optimize content for mobile devices, ensuring a smooth user experience on smartphones and tablets.
Advantages of CDNs
- Improved Performance: CDNs reduce latency, speeding up content delivery to end-users.
- Enhanced Reliability: They increase content availability and reduce the risk of server failures.
- Scalability: CDNs can handle traffic spikes and growing user loads effectively.
- Bandwidth Savings: They reduce data transfer costs by caching content on edge servers.
- Security: Many CDNs offer DDoS protection and security features to safeguard content.
- Global Reach: CDNs are designed to ensure that content can be accessed globally using a network of servers distributed worldwide.
Disadvantages Of CDNs
- Cost: High-traffic websites can incur significant costs when using content delivery networks (CDNs).
- Complex Setup: Implementing a Content Delivery Network (CDN) can be complex and may involve changing your existing infrastructure.
- Cache Invalidation: Ensuring that cached content is updated in a timely manner can be complex.
- Potential Data Privacy Concerns: CDNs may store user data, which could raise privacy issues.
- Limited Control: You may need more control over the network and caching policies.
- Single Point of Failure: If the CDN experiences issues, it could impact content delivery.
Specialized Networks
Various types of specialized networks are designed to serve specific purposes or industries. These networks often have unique requirements and characteristics tailored to their intended use. Here are some examples:
1. Extranet
An extranet is a communication network based on the internet protocol, allowing information sharing among authorized users. Individuals with valid login credentials are the only ones granted access to the extranet. It operates as a lower level of internetworking and falls into the category of a Metropolitan Area Network (MAN), Wide Area Network (WAN), or another type of computer network. Unlike a Local Area Network (LAN), an extranet requires at least one connection to an external network.
2. Intranet
An intranet is a private network that only an organization’s employees or members can access. Its primary purpose is to facilitate information and resource sharing within the organization. Intranets enable collaboration through group work and teleconferencing features. They secure a platform for internal communication within the organization, enhancing productivity and streamlining workflows.
| Feature | Intranet | Extranet |
| Access | Only accessible to employees | Accessible to employees and authorized partners or customers |
| Content | Contains confidential information | Contains less confidential information |
| Security | High-security | Medium security |
| Management | It Can be difficult to manage | It Can be easier to manage than an intranet |
| Cost | Implementing and maintaining can be costly. | Implementing and maintaining can be more cost-effective than an intranet. |
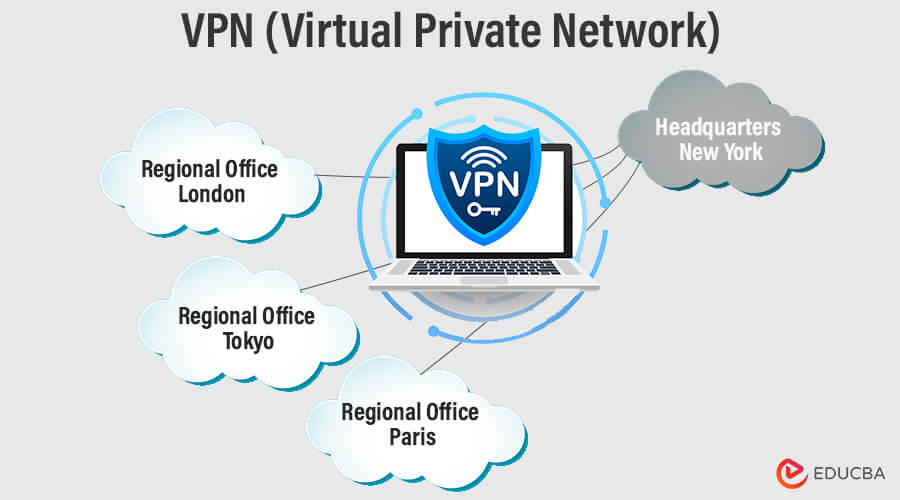
3. VPN (Virtual Private Network)
When a user connects to a VPN, it establishes a secure and private connection between their device and the network they are accessing. This tunnel encrypts and protects data transmitted between the user and the network, ensuring protection from potential threats. It encrypts the data traffic passing through the tunnel, ensuring confidentiality and protecting it from eavesdropping or unauthorized access.
Purposes of VPN:
- Secure Remote Access: Allowing remote users to connect to a private network from anywhere securely.
- Privacy and Anonymity: Concealing the user’s IP address and online activities from potential surveillance or monitoring.
- Bypassing Geo-restrictions: Enabling access to geographically restricted content or services by masking the user’s location.
Types of VPN Protocols and Technologies:
VPNs utilize various protocols and technologies to establish secure connections. Some common types include:
- IPsec (Internet Protocol Security): IPsec provides a suite of protocols for securing IP communication. It provides strong encryption and authentication and is usable in both remote access and site-to-site VPN configurations.
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): SSL and its successor TLS are widely used protocols for securing web communication. Users often use SSL/TLS VPNs for remote access to connect to web-based applications or services securely.
- OpenVPN: OpenVPN is an open-source VPN protocol that uses SSL/TLS for encryption and provides secure remote access. It is known for its flexibility and cross-platform compatibility.
- L2TP/IPsec (Layer 2 Tunneling Protocol/IPsec): L2TP combines the best features of PPTP (Point-to-Point Tunneling Protocol) and Cisco’s L2F (Layer 2 Forwarding). It commonly uses IPsec for secure remote access and provides strong encryption.
- PPTP (Point-to-Point Tunneling Protocol): PPTP is an older VPN protocol that offers basic encryption and authentication. While widely supported, it is considered less secure than other options.
Conclusion
In this interconnected world, understanding the diverse types of networks empowers us to harness their capabilities, explore new opportunities, and navigate the ever-expanding frontiers of the digital age. Whether connecting people, devices, or systems, networks are the threads that weave us together, enabling collaboration, information sharing, and transformation on a global scale. Let’s embrace and leverage the power of networks as we embark on a journey toward an interconnected future where the possibilities are limitless.
Recommended Articles
We hope that this EDUCBA information on “Types of Network” was beneficial to you. You can view EDUCBA’s recommended articles for more information.