Updated May 30, 2023
Introduction to Trunk Port
In this post, we’re going to look at what the trunk port is? Trunking is the term which is used in IT and telecom industries to refer to the network configuration to pass the data between the sender and receiver in the multiple entities medium. Take an example of how the tree trunk carries the water to every branch, similar to network trunk also multiple data and delivers to the correct location.
The switch port carries traffic more than once in the one VLAN is term as Trunk port. In terms of having a group of VLANs are sending the traffic here, one switch port will manage it. It will be much useful for the user who exchanges the traffic between two or more switches to have two or more VLANs configured in a single network. When identifying the traffic, the 802.1 Q tag or the common technique Inter-Switch Link tags, also named ISL, are used.
What is Trunk Port?
The trunk port will be carrying the signal traffic of all VLANs, which access to the specific switch is called Trunking. The trunk port marks the tag to the frame as 802.1 Q tag or the common technique Inter-Switch Link tags, also named ISL, when they moved between the switches. Hence every single frame can be reached to designate VLAN.
The Ethernet can act as either an access port or a trunk port when it is sending packets, but it would not occur at the same time. So that trunk port is configured here to send packets from more than one VLANs without having the traffic.
The packet needs to send/deliver in an accurate destination from more than one number of VLANs, and it can be done using the tagging or ISL, it is also known as encapsulation. Tagging would be done when sending the packets; the tag will be inserted in the header of frames. What are the details contained in the tag? it will include the sending id, port and switch details. The packet will reach the correct system using the tagging id within the multiple numbers of VLANs and switches. Here the encapsulated method plays a vital role to manage or permit the traffic in the network.
By default, the trunk port access all the VLANs, and it will permit for trunking. But, it will stop the traffic from particular VLANs from passing over the trunk by removing VLANs from a comprehensive list.
Trunking Mechanism
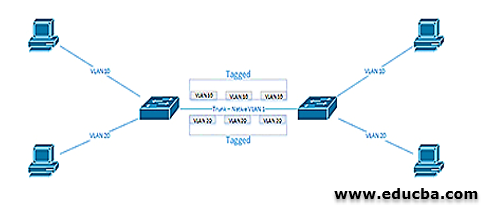
The primary mechanism is to trunking the devices that allow the traffic from more than one VLANs transported across a trunk in the modern switches. Here the task is the two different methods: one is the native VLAN, and another one is the tagging mechanism. The traffic sends between the devices without adding anything (like tag) is called Native VLAN. The default settings in the native VLAN, the switch is set to VLAN 1, and the settings allow the traffic send between all the port of more than one switches without any additional configuration. The tagging mechanism is adding the tag to the frame header in the Ethernet interface.
The above diagram shows all the traffic between the PCs in VLAN will be tagged to reach the destination address.
Why Trunking is Important to Configure with VLAN?
In the VLAN trunking, it is possible to extend into the entire network. But when multiple numbers of VLANs are connected in the network, it is necessary to ensure the singles are reaching the destination address. It is more complicated when more than one VLAN is connected to a single port.
In terms of having multiple VLAN configured in a single port, the system has to understand and route the signals. Here, the trunking VLAN is used to mark the tag in the header of the frames to support reaching the destination. So what does the tag includes? It includes a Media Access Control (MAC) address). It will help the frames to reach the respective destination endpoint system using the trunking link and host port. Sometimes, when working for multiple vendors, how trunking can be possible and what kind of mechanism can be used? Yes, the Cisco VLAN Trunking Protocol is used for it. So when we are configuring the VLAN in the VTP server, it will automatically distribute the packets between the switches, and it will reduce our configuration time.
Sometimes the trunking is used during maintenance activity. When there is some change happening for the network topology, the switch-forward must be up-to-date, so the trunking mechanism can be used.
They are using two types of trunking mechanism:
- Symmetrical trunking: It will send the packets to any ports; here, the transmission rate is very high.
- Asymmetrical trunking: It will send the packets using one port in the switch.
Use of Trunk port
- It can transmit data from multiple VLANs.
- If we have more than one switches or a network of switches in the organization, we just implement a single link to replace it by using any cables.
- Here the latency is lower.
- All will allow sending all the signals in each switch in a single trunk link.
- The bandwidth is very high.
Conclusion
We have learned about the trunking meaning in the computer network, introduced and explained the trunk port, the mechanism to be used, the purpose and use of the trunk port.
Recommended Articles
This has been a guide to What is a Trunk Port? Here we discuss the introduction, trunking mechanism, and why trunking is important to configure with VLAN? You may also have a look at the following articles to learn more-