Updated March 14, 2023
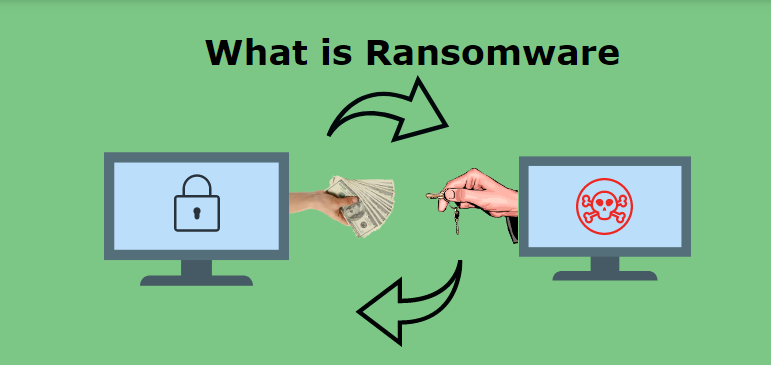
Introduction to Ransomware
Ever come across the term “ransom”? Ransom is usually a large sum of money demanded in exchange for someone or something. For example, it is commonly used in kidnapping cases where the kidnapper demands a ransom in exchange for the hostage. Ransomware, or as one might refer to it as “ransom malware”, is no different. It is a malware type that blocks one’s access to their own system resources or threatens to make the victims sensitive data public if a ransom is not paid. Its roots can be traced back to the late 1980s. The first malware of this kind was written by Joseph Popp in 1989 and was known by the name of “PC Cyborg”.
However, back then, ransomware wasn’t a big threat as anyone with a decent knowledge of computers could easily reverse the malware and have the issue fixed. Unfortunately, with time, ransomware has evolved to the stage where one cannot reverse it without obtaining the decryption key.
How Ransomware Works?
- Cryptography plays a vital role in the functioning of ransomware. On a more precise note, it is Cryptovirology – a branch of cryptography that specializes in designing malicious software. Cryptovirology makes use of cryptography features to encrypt and decrypt data with the help of keys. Ransomware encrypts the victim’s data making them unreadable, hence unusable and corrupt. It then demands a ransom in exchange for the key, which can decrypt your data and make it usable once more.
- This technique is well known by the name “cryptoviral extortion”. Decrypting the affected data without the decryption key is impossible in this case. Instead, ransoms are demanded in the form of digital currencies such as cryptocurrencies, for example, bitcoins, to help make sure the transactions remain untraceable. The perpetrators take advantage of this currency exchange procedure to avoid being tracked down.
How can my System get Infected by Ransomware?
Ransomware usually spreads via human interactions with the internet over a browser. It could be disguised as attachments or links in an e-mail which a user might click on out of sheer curiosity. It could also be part of an online advertisement or links on a website that would lead to a malicious website or download the malware into one’s system under the pretext of downloading another file the victim would otherwise find useful.
However, there have been instances where ransomware was able to navigate from one system to another without any human intervention. For example, the “WannaCry” ransomware which created havoc in early 2017, had infected as many as 200,000 computers across 150 countries.
Types of Ransomware
Here are some types of Ransomware that you should be aware of:
1. CryptoLocker
This ransomware targeted Operating systems running on Microsoft Windows. It would migrate as attachments via e-mail. It was highly active for a brief period from 5 September 2013 to late May 2014. However, in this brief period of time, a total of $3 million dollars was believed to have been exported from the victims. Though it was taken down in May 2014, it is provided as the base foundation for much more future ransomware’s yet to come in the market, such as CryptoWall, Torrent Locker, etc.
2. Jigsaw
Initially developed in 2016 was known as the “BitcoinBlackmailer”. It encrypts one’s data and proceeds by deleting them at regular intervals unless the ransom is paid for. An hour is provided to the victim for payment of the ransom. The first file is deleted after this initial hour if the ransom is not received. Here forward, the number of files deleted increases exponentially on non-receipt of the ransom claimed. The victim has a maximum of 72 hours to shell out the ransom, after which all files are deleted.
3. Petya
It directly attacks the computer booting mechanism by corrupting the master boot record and executing a payload that prevents the booting system. This ransomware targets windows systems.
4. KeRanger
This ransomware is designed to attack Mac OS computers and has affected over 7000 systems using Mac. It encrypts your files and data while demanding a ransom in return for decrypting the same.
5. ZCryptor
It infiltrates the system by disguising itself as an installer of required software. Once installed, it affects external drives and flashes drives to propagate further onto other computers. After which, it encrypts files by adding an extension .zcrypt to the file.
Detection and Prevention
- One should make use of anti-ransomware software to detect ransomware intrusion at an early stage.
- For example, Cyberson provides free software “RansomFree” designed to find and prevent ransomware attacks.
- There are a few more in the market; these are CyberSight’s Ransom Stopper, Check Point’s zone alarm anti-ransomware, CryptoDrop’s anti-ransomware.
- These software’s get triggered when they detect a file being encrypted. They also rely on other typical behaviors of ransomware to spur into action.
Preventive Measures
Few preventive measures to be taken are:
1. Backup
Make sure to take back up your files from time to time and save it on another external hard drive or remotely on the cloud. This way, data loss can be avoided due to many other possible failures such as system crash and not just ransomware.
2. Updating OS Versions
One should keep their systems updated to the latest OS version release as these releases tend to have updates that can block ransomware attacks or make them less catastrophic in nature.
3. Using Anti-Ransomware Software’s
Securing your system with anti-ransomware software helps take preventive measures at an early stage of the attack. Also, one should keep the anti-ransomware software updated and scan one’s system at regular intervals.
4. Block Unknown E-Mails Addresses and Potentially Harmful Websites
Preventing such malicious e-mails and links responsible for the attacks can help nip the problem at its bud. This setting can be customized using one’s anti-virus settings.
How to Remove Ransomware?
Once infected, you have only three options to look out for:
- Format and Restore Backed-up Files: Make sure to format and scan for ransomware. Delete any files found affected, and then restore the data from your backup.
- Use Decryption Software: If ransomware is less severe, one might be able to find a decryption tool that can help decrypt the affected files without paying a ransom.
- Settle the Ransom: Since the more sophisticated ransomware cannot be decrypted using the free decryption tools available online. Therefore, one might have to pay the ransom. It should also be noted that paying the ransom does not guarantee that one will be able to revive the data.
Recommended Articles
This is a guide to What is Ransomware? Here we discuss the introduction, working, types, detection and prevention of Ransomware respectively. You can also go through our other suggested articles to learn more –







