Updated September 29, 2023
Introduction to SFTP
Today’s digital landscape demands secure data communication. Secure File Transfer Protocol emerges as a critical option for protecting sensitive data in transit. In this article, we will delve into the complexities of SFTP, exploring its mechanisms, benefits, setup procedures, and real-world applications to comprehend its critical position in current cybersecurity.
Table of Contents
- Introduction to SFTP
- What is SFTP?
- How does it work?
- How to Transfer File?
- List of Common SFTP commands
- Advantages
- Disadvantages
- Security Measures
- Difference Between FTPs vs SFTP
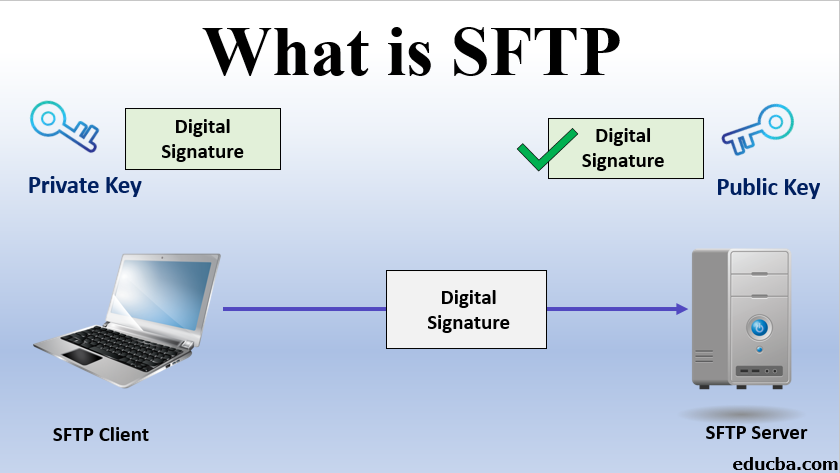
What is SFTP?
Secure File Transfer Protocol is an encrypted and secure means of transmitting files between systems across a network. Unlike its predecessor, FTP (File Transfer Protocol), SFTP employs advanced security measures by utilizing encryption techniques to safeguard the integrity and confidentiality of data during transit. SFTP operates on a secure channel, usually through SSH (Secure Shell), which provides an underlying transport protocol. This combination ensures that critical information is protected from unauthorized access and eavesdropping while being transmitted between the client and server.
How does it work?
Secure File Transfer Protocol is designed to provide a secure and reliable way to transfer and manage files over a TCP/IP network. It builds upon the foundation of the SSH (Secure Shell) protocol to ensure data confidentiality, integrity, and authentication during the file transfer process. Let’s break down the key components and processes involved in how SFTP works:
- Secure Data Transfer: SFTP is designed to address the security vulnerabilities of traditional FTP. It encrypts the transferred data, preventing unauthorized access and eavesdropping during transmission. Encrypting the data packets, the content remains indecipherable even if intercepted by unauthorized parties.
- Similarities to FTP and Linux Shell Commands: SFTP uses commands similar to the standard FTP protocol. Many SFTP commands mirror common Linux shell commands, making them intuitive for users familiar with command-line interfaces. This allows users to perform tasks like listing directories, transferring files, creating directories, and managing files in a manner consistent with their experience on Linux systems.
- Tasks and Capabilities: SFTP serves various purposes, including transferring sensitive files securely, resuming interrupted transfers, and managing files on remote servers. It empowers users to upload files from their local machine to a remote server or download files from the server to their local machine.
- Connection Establishment: To establish a connection with an SFTP server, clients connect to the standard SSH port, usually port 22. This connection initiates an SSH session that shows a secure and encrypted communication channel linking the client and the server.
- Client-Server Relationship: SFTP involves both a client and a server component. The SFTP client is software users connect to a server and manage files. Users can store, retrieve, and manipulate files on the SFTP server. When a user interacts with the client and requests a file transfer, the client initiates a secure communication channel with the server.
- Data Encryption and Decryption: SFTP uses encryption algorithms to securely move data between the client and the server. These algorithms ensure that the data remains unreadable and confidential during the transfer. This encryption guarantees that sensitive information, such as passwords or file content, remains protected from unauthorized access.
- Authentication with SSH Keys: SSH keys are commonly used to automate server access and enhance security. In SFTP, users can use SSH key pairs for authentication. One-half of the key pair (the private key) is stored on the client device, while the other half (the public key) resides on the server. When the keys match, the user is authenticated, allowing secure access without the need for passwords.
- Secure Connection Establishment: SFTP utilizes an SSH data stream to establish a secure connection between the client and the server. This connection ensures that all data transferred between the two endpoints is encrypted, maintaining the confidentiality and integrity of the exchanged files.
- Choice of Authentication Methods: SFTP provides flexibility in terms of authentication methods. Users can authenticate using various ways, including a user ID and password, SSH keys, or both. This allows organizations to implement security measures that suit their specific needs.
- Acknowledgment and Completion: During file transfers, SFTP sends acknowledgments to the client, confirming that the data has been successfully received and stored on the server. Once the transmission completes, the client can disconnect from the secure connection.
- Session Termination: When the client has completed its tasks, it can gracefully terminate the SFTP session, disconnecting the secure channel and releasing any assigned resources.
How to Transfer File by Using SFTP?
Here’s a step-by-step guide to the SFTP workflow:
Step 1: Prepare Your Environment:
- To connect with the SFTP server, you must first open a terminal or command prompt on your local machine.
- It is essential to ensure you have the required credentials, such as username and password or private key, to access the server.
Step 2: Initiate the SFTP Session:
- To begin an SFTP session, enter the following command in the terminal:
sftp username@server_address- Replace username with your SFTP username and server_address with the server’s hostname or IP address.
- If you’re using key-based authentication, enter the passphrase for your private key when prompted.
Step 3: Navigate Directories:
You’ll see a sftp> prompt when you’re connected. To navigate directories, use common Unix-like commands like:
- ls: To view the files and directories in the current remote directory
- cd directory_name: If you want to change to a specific directory on the remote server
- pwd: To display the current remote directory.
Step 4: Upload Files to the Server:
- To transfer a file from your computer to the server, use the “put” command.:
put local_file remote_directory- Replace local_file with the path to the file on your local machine and remote_directory with the destination directory on the remote server.
Step 5: Download Files from the Server:
- To download a file from the server to your local machine, use the get command:
get remote_file local_directory- Replace remote_file with the remote server’s file path and local_directory with the target directory on your local system.
Step 6: Other Useful Commands:
- mkdir directory_name: To create a directory on the remote server
- rm file_name: To delete a file on the remote server
- rmdir directory_name: To remove an empty directory on the remote server
Step 7: Close the SFTP Session:
To end the SFTP session, type exit or bye.
List of Common SFTP Commands
SFTP uses a set of commands similar to traditional FTP (File Transfer Protocol). However, these commands are sent securely through the SSH tunnel. Some common SFTP commands include:
| Command | Description |
| put | Upload a file from your local system to the remote server. This command transfers files from your computer to the remote SFTP server. |
| get | Download a file from the remote server to your local system. This command retrieves files from the SFTP server to your computer. |
| cd | Change the active directory path on the remote server. This allows you to navigate to different directories on the server. |
| pwd | Display the current remote working directory. It shows you the directory you are currently in on the remote server. |
| Icd | Change the local system’s directory path. This command allows you to navigate to different directories on your local system. |
| lpwd | Display the current local working directory. It shows you the directory you are currently in on your local system. |
| ls | Display the contents of the remote working directory. It lists the files and directories in the current directory on the remote server. |
| lls | Display the contents of the local working directory. It lists the files and directories in the current directory on your local system. |
| lmkdir | Create a local directory. This command creates a new directory on your local system. |
| lumask | Change the umask value for newly created local files and directories. The umask determines the default permissions for new files and directories. |
| rename | Rename a file on the remote host. This command allows you to change the name of a file on the remote server. |
| rm | Delete a file on the remote host. It’s used to remove files from the remote server. |
Advantages
Below are the different advantages:
- Security: SFTP is well-known for its high levels of security. During transmission, it encrypts data to prevent eavesdropping and unauthorized access. SSH authentication offers secure user verification, making it highly resistant to hacking and data breaches.
- Authentication Methods: SFTP supports a variety of authentication techniques, including password-based, public key, and multi-factor authentication (MFA). This adaptability enables organizations to select the level of protection that best meets their needs.
- Data Integrity: SFTP protects data integrity through built-in integrity checks during file transfers. This means that transferred files are validated to be unchanged, lowering the chance of data corruption.
- Portability and Platform Independence: SFTP is available on various platforms and operating systems, giving it a versatile alternative for organizations with diverse settings. Clients and servers can interact without concern for the underlying systems.
- Firewall and NAT Friendly: SFTP runs over a single secure connection, making it compatible with firewalls and Network Address Translation (NAT). Unlike FTP, which requires separate control and data connections that may cause firewall problems, SFTP’s single connection simplifies network configurations.
- Automated File Transfers: SFTP is easily integrated into automated processes and scripting, making it useful for scheduled or batch file transfers, backups, and data synchronization.
- Compliance Requirements: SFTP is frequently used to meet compliance standards such as PCI DSS, HIPAA, and GDPR, which require safe data transfer and storage practices.
Disadvantages
Below are the different disadvantages:
- Complex Setup and Management: Compared to regular FTP, setting up and installing an SFTP server and handling SSH keys can be more difficult. Organizations may require additional skills to ensure proper implementation.
- Performance Overhead: Compared to unencrypted file transfers, the encryption and decryption processes during SFTP transfers can cause performance overhead. However, advances in encryption technologies have mitigated this concern.
- Compatibility and Adoption: While SFTP is commonly supported, legacy systems or outdated software may not support SFTP. Compatibility concerns could develop in such circumstances.
- Limited Directory Listing Support: Unlike FTP, the secure nature of SFTP makes it more difficult to provide extensive directory listings. While SFTP can still give directory listings, client and server implementations may vary.
- Learning Curve: It may be necessary for users and administrators to become knowledgeable about the SFTP command-line interface or client software, but this could be Learning Curve for those who are used to working with traditional FTP.
Security Measures
Security is of the utmost significance when using the Secure File Transfer Protocol (SFTP). This section outlines the implementation of critical security measures required to protect data confidentiality, integrity, and availability during file transfers.
1. Hardening the SFTP Server
Hardening the SFTP server means improving its security by reducing potential vulnerabilities. Consider the following steps:
- Disable Unused Services: To enhance server security, we recommend disabling any services or protocols that are not in use.
- Regular Software Updates: Regularly updating the operating system and SFTP software with the newest security patches is critical to address known vulnerabilities.
- User Privileges: When assigning user privileges, it is best to assign users only the minimum necessary privileges for their specific tasks. Avoid using the root account for SFTP activities.
- Firewall Configuration: Configure firewalls to restrict incoming and outgoing network traffic to only essential SFTP ports and IP addresses. This will help to reduce the attack surface and make your server more secure.
2. Network Security
Ensure secure data transmission and network access for SFTP by considering these measures:
- SSH Encryption: Use vital encryption techniques for the SSH connection to prevent data eavesdropping during transit.
- Virtual Private Networks (VPNs): To enhance security, VPNs are recommended to encrypt all traffic between the client and server, providing an additional layer of protection.
- Demilitarized Zone (DMZ) Setup: Place the SFTP server in a DMZ to isolate it from the internal network and reduce potential attack vectors.
3. Data Protection
Ensuring the protection of the transferred data remains a primary concern. Implement these safeguards:
- Encryption at Rest: Encrypt files on the server at rest to ensure the data stays secure even if the server is compromised.
- Transit Encryption: To avoid unauthorized interception, enforce the usage of encryption during data transfer.
- Data Integrity: Implement checksums or digital signatures to ensure that files remain unmodified after transfer.
4. Monitoring and Auditing
Maintain visibility into SFTP activities and detect potential security breaches:
- Logging: Enable logging of SFTP sessions in detail, including login attempts, file transfers, and administrative tasks.
- Auditing: Regularly review logs for anomalies or suspicious activity, and take necessary action upon identification.
5. Regular Security Audits
Periodically perform security audits and assessments of the SFTP environment:
- Vulnerability Scans: Run vulnerability scans regularly to uncover any server configuration flaws.
- Penetration Testing: Engage in ethical hacking to simulate possible attacks and uncover vulnerabilities that automated scans may not identify.
6. Employee Training
Ensure that your staff is well-trained in security best practices:
- User Education: Train users on secure password practices, recognizing phishing efforts, and ensuring the security of their private keys.
- Security Awareness Programs: Regularly update employees on emerging security threats and educate them on the importance of following security rules.
Difference Between FTPs vs SFTP
| Factor | FTPS (FTP Secure) | SFTP (SSH File Transfer Protocol) |
| Protocol | FTPS is an extension of FTP | SFTP is a separate protocol |
| Security | Relies on SSL/TLS encryption | Uses SSH for encryption and authentication |
| Port | Typically uses port 21 (control) and port 989/990 (data) | Typically uses port 22 |
| Authentication | Supports various authentication methods, including username/password, certificates | Primarily uses public key authentication |
| Key Management | Involves managing SSL/TLS certificates | Requires managing SSH key pairs |
| Data Encryption | Data can be encrypted during transfer (optional) | Data is encrypted by default during the transfer |
| Data Integrity | Limited integrity checks | Provides built-in integrity checks |
| Firewall/NAT Support | May require additional configuration due to separate control and data connections | Easier to configure through firewalls and NAT |
| Platform Independence | Available on multiple platforms | Also available on various platforms |
| File Listing | It may require additional configuration for secure directory listing | Secure directory listing is inherent |
| Server Software | Supports multiple server software options (e.g., ProFTPD, vsftpd) | Usually uses OpenSSH server or similar |
| Client Software | Different FTPS clients are available | SFTP clients are widely available |
| Compliance | Commonly used for PCI DSS compliance | Commonly used for regulatory compliance |
Conclusion
SFTP is one of the best protocols that provide data security and transmit data. It can transfer the data by just dragging the files with lightning speed. It is efficient and hence is used very widely. If you wish to send files to a user or another server, SFTP is the solution.
Recommended Articles
We hope that this EDUCBA information on “What is SFTP” was beneficial to you. You can view EDUCBA’s recommended articles for more information.