Updated April 18, 2023
Introduction to Man in the Middle Attack
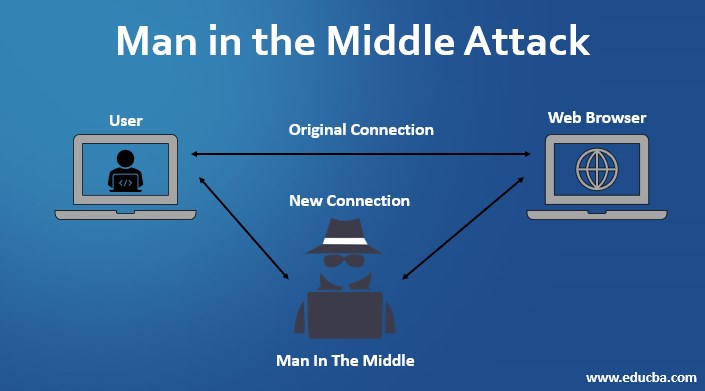
Yes. I know. The title seems scary. But it is not the name of some movie. But I can bet it is as scary as it gets. Man in the Middle (MITM) is an attack used in hacking and network hijacking.
Man-In-The-Middle Attack (MITM) Synopsis
Let me explain this to you. Assume that you are a person who is required to do site visits regularly for your company for some x type of job. You visit your client’s place and attach your dongle to start the internet.
But you failed to recharge your internet package (just assume). And now you cannot even recharge it due to the fact that your internet is down.
Now the client is good enough to allow you to access his Wireless LAN or Wi-Fi. But the thing is, is this safe? Absolutely not. You, my friend, can now be a victim of some big corporate espionage. Not exactly, but my point is just that it’s not safe. Let me explain it to you in some other manner.
What I told you above was just a warning. I have done this in real life, and let me show you the consequences of that. To begin with, I am a Penetration tester.
I SUGGEST YOU DO whatever I am going to say here in your own home environment or lab. Doing this in a public place can put you in some serious legal issues. (In short, unless you have a good lawyer, don’t do this).
The Incident
Two years ago, when I was still learning to hack (I still am learning), I was sitting in a Mcdonald’s in Pune, India. My internet was down that week due to extreme rainfall. And since I am a person who cannot live without the internet, I decided to crash at a McDonalds, the reason being it has FREE Wi-Fi.
Yes, People normally jump straight away into a place where there is free internet (at least people in India do) without thinking about the problems it can cause (because of people like me).
So, I started my laptop. I had installed Arch Linux then, which is still my favorite. But what I did could be done on any laptop installed with basic Linux OS (YES-Its Linux). I was bored, and since I had nothing to do, I started a MITM attack on a fun basis. This attack is pretty sophisticated.
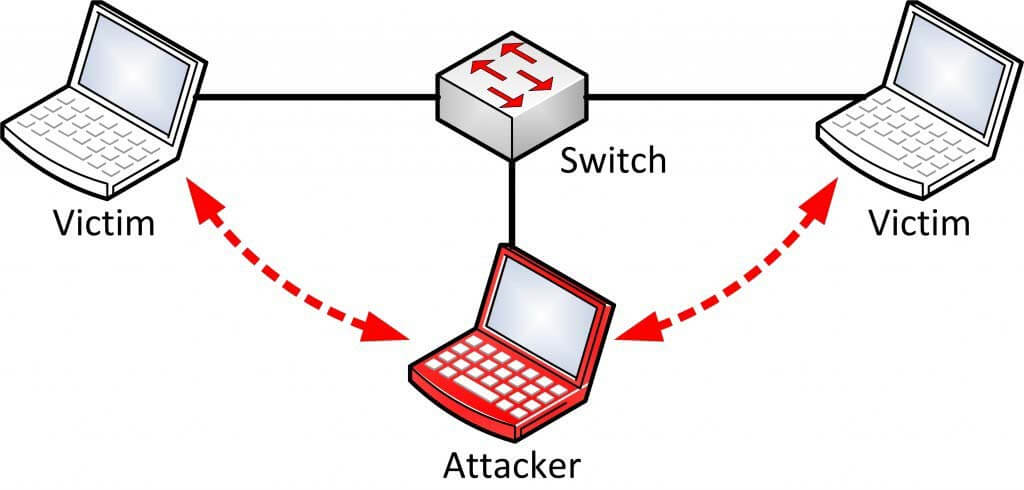
This would probably make other computer and cell phone users think I am the router and pass all the packets through me. If you are not horrified about this, then you should be.
The reason is that now I handle every piece of information that passes through the network, both incoming and outgoing traffic. Now I can view the packets, sniff them and look through all the data passing through.
Whether people log on to social networking websites, people chatting with each other, or worse, people doing banking transactions. I would normally stay away when I saw any bank’s digital certificate. But what I would do just for fun sake is I would modify the chats that people used to do.
This was seriously fun. WhatsApp is Secured (or at least you cannot crack it as soon as it passes through the network). Many people used to use WeChat and Hike, which had extremely low or no encryption. So, when a guy used to ask a girl to meet somewhere, I would usually change their meeting address.
I know this is childish, but as I said, it was fun. (I did much more than just this). So, the thing is, I could not only see the transactions and traffic happening, I could even change them and send something totally off the charts.
For example, if someone plays a video on YouTube, I could change that video with some simple JavaScript and troll them. Now, let me ask you again about my first example of using random Wi-Fi. Do you think that is secure?
The How to and Why
Okay, now the main question you all have been waiting to ask? Why? It is probably not even a question. There are a lot of answers for that, like to make yourself secure or to understand the risks involved and the science as to how it works in reality and how to know and catch anyone doing the same stuff to you.
So, to start with, to make a MITM attack, I recommend using Kali Linux. That way, there is much less hassle for you to install anything because Kali Linux is a pen-testing software that comes with almost every pre-installed tool.
MITM is normally performed using ARP poisoning. MITM includes cookie stealing and session hijacking, where you can capture any person’s whole login session.
With enough information, one can perform a Distributed Denial of Service attack and down the whole network. I won’t be writing down full-fledged pieces of code here. But I will tell you the basics of MITM to get you started. The reason for that is that the attack mostly depends on the router’s security.
You just cannot take a laptop these days and hack into something. It would help if you had a proper setup for that. So, after installing Kali Linux, I recommend good monitoring and injecting Wi-Fi.
The one I have been using for months is TP-Link Wn722n. It has a good range and is extremely powerful and portable to make a MITM attack.
Now all you need to do is use ArpSpoof to spoof your Mac ID to let the network think you are the router and then capture all the packets via Wireshark and tcpdump. You can also sniff the traffic with Dsniff, but however, you won’t be able to sniff https packets.
Dsniff only works with an unsecured socket layer, i.e. HTTP, and not https. To work with HTTP, you need to use SSL Strip to discard the Secure sockets layer and then sniff the packets through it.
There are a few more things to keep in mind. Make sure that your firewall is configured to accept these packets. If you are doing this on LAN, it’s not an issue, but if you are trying to do this on a WAN, you would have to port forward it to get these packets.
Following are a few MITM Attack Tools that can be used:
For Windows
Cain and Abel – A GUI tool for sniffing an ARP Poisoning. Since I have been in this field for a long time, I would rather suggest not going for the man-in-the-middle attack tools for Windows. If you are trying to make multiple attacks, Windows won’t help. You will have to switch to Linux or have multiple computers, which is not good.
For Linux
- Ettercap and Wireshark: To sniff packets on LAN
- Dsniff: To capture SSH logins
- SSLStrip: To remove the secure layer over packets
- Airjack: To do Multiple MITMs at one go
- Wsniff: A tool for SSL and HTTPS removal
If you thought this was it, wait. There is one more platform most of you may not even know of: And it’s my favorite Android. Let’s see what Android has in its store:
- Dsploit: A tool for just Different types of MITM attacks
- Zanti2: Zanti is commercial software. Previously, it was a paid app, but recently they have made it freeware. It is extremely strong in the case of MITMs and other attacks.
- Wireshark: Same as Linux
- Kali Linux: Yes. Kali Linux is available for Android, now known as NetHunter. The best part is you can even ssh into your own home computer with that and then start the hacking without leaving any trace.
So, next time you see anyone messing around your network, it’s not just a guy with a laptop you must be doubtful of. Any person with a good Android Cellphone like the Nexus or the One Plus can hack into your network without even you knowing that.
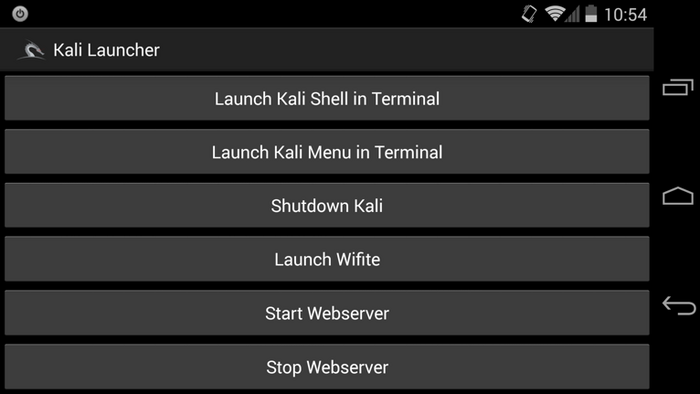
This is what the GUI of Kali on Nethunter looks like:
Image Source: kali.org
Paranoia is the key to Security.
The only way to stay secure in this parasite-ridden world is to stay paranoid. It’s not just for Man in the Middle Attack, but because it’s for everything. Following are a few steps that you can consider when accessing public Wi-Fi to keep yourself secure:
- Always use a VPN when connecting to email Services.
- Use a secure email with decent security to detect malware, e.g., Google or Protonmail.
- If you are a Public Wi-Fi owner, you should install an IDS, i.e. Intrusion Detection System, to capture any non-normal activity.
- Check your credentials every now and then to see if any random activity has occurred or if it has been accessed from some other location. Change your passwords every month. And most importantly, don’t make them easier for people to crack. Most people keep passwords like 18two19Eight4. This password is extremely easy to crack; the reason being this can just be a birth date, i.e. 18th Feb 1984. Passwords should be like ‘iY_lp#8*q9d’. Yup, this is what a decently secure password looks like. I am not saying this is uncrackable. But, it will consume 10 times more than the time it takes in the case of the prior.
Recommended Articles
Here are some further articles to learn more: